MICROCOMPUTERS FOR INFORMATION
RESOURCES MANAGEMENT
A GUIDE TO THE VITA SYSTEM
by
Gary L. Garriott, Ph.D.
Brij Mathur, B.A.
Helen Picard, M.A.
and
Richard S. Muffley, M.S.
published by
Volunteers In Technical
Assistance
1600 Wilson Boulevard, Suite 500
Arlington, VA 22209, USA
September 1983
Revised August 1984
Volunteers In Technical Assistance
1600 Wilson Boulevard, Suite 500
Arlington, VA 22209, USA
[C] September 1983
TABLE OF CONTENTS
I. Introduction
Background
Program
Design
Goals of
the Training
II. System Overview
Some
Definitions
Booting Up
Program
Languages
Operating
System
III. Basic
Operations
Turning On
the Computer
The
Keyboard
Creating
and Storing Files (Information)
D.O.S.
Commands
Menus
Password
Protection
Floppy Diskettes
Editing
Files and Programs
Variables
Data Bases
IV. Using the
Microcomputer
Data Entry
Procedures
for Data Entry
Getting
Started
Logging
On
Entering the Data
The
Cursor, Data Fields, and
Key
Operations
Updating
Records
Printing
Data
Data Base
Searching
Bibliographic Files
Procedures for Bibliographic Data Base
Searching
VITA
Volunteer Files
Sample
Volunteer File Search
Commercial
Data Bases: DEVELOP (CDC)
Key Word
Searching
Truncation
Using
"AND," "OR," and "AND NOT"
The
Report Following the Search
Reading
the Result File
Computer
Software: Other Applications
Financial Records
Graphics
Long
Distance Computer Links
Games
Educational Tools
V. Automating an
Information Service
Considerations for Computerization:
Myths and
Realities
Questions for
Potential Users
Questions to
Ask Computer Salespeople
Technical
Considerations for Field Use
of
Microcomputers
Appendixes
A.
"In Other Words"--a glossary of
computer terms
B.
VITA Bibliographic Data Base format
C.
VITA Volunteer File format
D.
DEVELOP Literature Unit
E.
DEVELOP Technology Unit
F.
DEVELOP Who's Who Unit
G.
Text Writing Program:
Input
H.
Text Writing Program:
Final Output
I.
Apple Plot graph
I. INTRODUCTION
Background
Microcomputers are becoming increasingly important for
the management of a wide variety of information resources.
VITA has made a major institutional commitment
to incorporating microcomputers into those aspects of
our work that will result in greater efficiency and
productivity, and, therefore, greater effectiveness.
We
view microcomputers as extremely useful tools for technology
development and transfer.
In addition, we are
now using microcomputer systems to enhance one of our
major activities--the transfer of technical information
overseas. As it
became apparent that computers could
improve our own operations, we sought ways to ensure
that institutions in developing countries could benefit
from our experience.
Our choices of hardware and
software were specifically guided by this concern.
Our Information Resources Management training reflects
this emphasis on computer applications.
It also
reflects our experience that extensive computer programming
expertise is not usually required to adapt
existing software, particularly file and data base
managers. Our
experience suggests that many organizations
will find that they can introduce, use, and maintain
successful microcomputer applications.
This text is an aid to understanding basic microcomputer
operations, using VITA's bibliographic and skills
bank systems as practical examples of functional
applications.
While our system is built around Apple computers,
a similar logical approach applies to all
microcomputer systems.
Program Design
The microcomputer training module emphasizes operations
and applications. It
does not require prior computer or
programming experience.
The course combines written
information with lectures, demonstrations, and practical
experience. Each
trainee will also receive individual
diskettes to maximize the opportunity for practice
on the computers.
Additional instruction will be
available for those who wish to gain more expertise in
the logical processes involved in the design of
microcomputer
applications.
Goals of the Training
VITA's microcomputer training module is designed to
provide each participant with the information, reference
materials, opportunities for group and individual
discussion, and practical experience that is necessary
for a basic foundation in computer applications and
operations. More
specifically, the course provides
trainees with:
*
an introduction to basic terms and concepts
common
to all computer
systems;
*
knowledge of basic computer operations,
including
such peripheral
equipment as disk drives and
printers;
*
practical experience with a computerized
skills
bank and
bibliographic data base, including carrying
out such tasks
as data preparation, data entry
and updating,
and data base searching;
*
a presentation of the factors necessary for
the
analysis and
appraisal of the potential for the
successful
introduction and operation of a microcomputer-based
system in an
organization; and
*
guidelines helpful in assessing which
microcomputer
system and
software package(s) are most suitable
for the given
problem and environment.
VITA is committed to assisting all trainees and their
sponsoring organization wishing to establish specialized
microcomputer systems and applications.
As a
result of our own experience in developing a complex
microcomputer-based system, VITA can offer valuable
assistance to anyone getting started with computers.
II. SYSTEM OVERVIEW
Some Definitions
In general, all computer systems consist of hardware
and software.
Hardware includes the keyboard and screen
of the computer itself, its peripherals (components
such as printer, disk drive, modem, hard disk, etc.),
and all other physical equipment making up the computer
and its total system.
Software is what makes this equipment work.
Software
consists of a program (or programs) written in any one
of several computer "languages" that makes the
computer
perform the task(s) required by the user.
Specialists
skilled in computer programming write such programs in
the language(s) suitable to the particular computer,
and physically place them on a disk or diskette.
Separate programs are generally required for each task
the computer will perform.
A disk is a storage medium similar to a phonograph
record. Disks are
used to store the instructions needed
to make the computer operate (the program), and to
store the data the computer will manipulate for the
user.
Information is stored in two areas in a microcomputer.
One area is in the computer itself and is referred to
as memory. The other
area is on a magnetic disk or
diskette. The
computer's memory is temporary, and
information stored in it is lost when the machine is
turned off.
Information stored on the diskettes, on the
other hand, is permanent.
It is not lost when the
machine is turned off.
It is easy to transfer information
from one storage area to the other (see LOAD and
SAVE in Section III).
Microcomputers use flexible, or "floppy" diskettes
that
are 5-1/4" or 8" in diameter, depending upon the
type
of microcomputer used.
One floppy diskette can store
120,000-130,000 characters.
When it is necessary to
store more data than this and to have a variety of
programs readily available, a hard disk can be used to
expand the storage capacity, or memory.
A hard disk can
store up to 80 million characters.
All of these computer
terms, and others, are defined further in Appendix
A, "In Other Words."
Booting Up
To function properly, the computer must
"understand"
the commands or instructions the computer operator will
use. Thus, the first
task of the operator is to program
the computer with the specific instructions for the job
at hand. The
operator selects the diskette containing
the proper program, or set of instructions, for the
language and the operating system that will be used.
When the machine is turned on, the information is
transferred from the diskette to the computer's memory.
This process is called "booting up."
The Apple computers used in this course read the program
language information from the diskette placed in
Disk Drive 1. Good
practice requires that the program
diskette be inserted into Disk Drive 1 before the
machine is turned on.
Program Languages
The Apple computer understands a variety of specialized
program languages, including FORTRAN, COBOL, PASCAL,
BASIC, and many others.
Only one language is used at a
time. If no language
information is specified, the
Apple computer assumes that the operator is using a
special form of BASIC that has been developed by the
Apple Corporation for its computers.
Operating System
The computer also uses special commands for carrying
out file and diskette operations.
The commands that are
required depend on the particular type of operating
system the computer has.
In this course, the machines
will be using either Apple D.O.S.
(Disk Operating
System) or CP/M (Control Program for Microcomputers).
During the "booting up" process the operating
commands
are added to the language commands given to the computer.
Though you will be using CP/M later during this
course, it will not be necessary to learn the operating
commands at this time.
However, you will need to learn
the operating commands for Apple D.O.S., which are
given later in this manual.
III. BASIC
OPERATIONS
Turning On the Computer
The red switch on the left of the computer turns on the
system. This switch
causes several things to happen.
The most noticeable is that Disk Drive 1 begins
whirring and a red light appears as the diskette is
being read. After a
few seconds, the whirring will
stop, indicating that the program instructions are now
complete, or "resident" in the computer's memory.
The screen will display a "prompt," which is a
bracket
(]). At this moment,
the prompt indicates that the
computer is ready to receive instructions from you.
Next to the prompt there is a flashing block called the
"cursor" that marks the point at which you will
type
the next character.
The Keyboard
The computer keyboard is very similar to a typewriter,
but there are differences:
1. The information
you type on the computer keyboard
appears on the
screen, but it does not enter the
computer memory
until you press the RETURN key. It
is the RETURN key
that actually sends your typed
command to the
computer.
2. All the letters
appear on the screen in upper case,
so the
"shift" key has a somewhat different function
from the
typewriter's "shift" key. Use
the
"shift"
key on the computer to type the top characters
on all keys
displaying two characters.
3. You can type a
character repeatedly by simultaneously
pressing the REPT
(repeat) key and the key
you wish to
repeat.
4. There are two
arrows on the right side of the keyboard.
The left arrow
moves the cursor backward and
erases the
characters it moves over. The right
arrow causes the
cursor to move forward but does
not erase the
characters it passes over.
5. The CTRL
(control) key is on the left side of the
keyboard.
When you press this key and certain other
keys at the same
time, special commands are sent to
the
computer. For example, if you type C
while you
press CTRL, the
computer stops what it is doing and
allows you to
enter new commands. This operation is
called Control-C
and is written CTRL-C. The key
labelled BELL
(the top character on the G key) also
is operated by
simultaneously pressing the CTRL
key.
This operation is referred to as
CTRL-G. When
you get to a
keyboard, type CTRL-G, CTRL-J, CTRL-M,
and others to see
their special effects.
6. Pressing the ESC
(escape) key has different effects
depending on the
state of operation of the Apple.
If a program is
running, typing ESC may interrupt
the program in
the same manner as CTRL-C. This will
put the computer
in a mode ready for a new operating
command.
However, if the screen shows a prompt
and a flashing
cursor, pressing ESC one time will
put the computer
in an editing mode.
7. Using the RESET
key is a drastic operation. This
key will usually
cause loss of the computer memory
and other
internal changes (nothing serious will
happen to the
hardware). If a program is written
poorly or is not
completely compatible with the
hardware being
used, running it may cause the computer
to
"hang-up" or "hang."
This means that the
computer is stuck
and will not respond to any key
or sequence of
keys from the keyboard. To get it
unstuck, press
the RESET key. The effect this will
have on the
software loaded into the computer is
uncertain, so use
RESET only as a last effort.
Creating and Storing Files (Information)
When you need to save information for future recall,
you place it in a file that is stored on a diskette.
Just as you might use a typewriter to record information
on paper, you can use the computer keyboard to
type information into the computer's memory, and from
there transfer it to a floppy diskette for permanent
storage. The floppy
diskette is like the piece of
paper; both contain images of information.
A file can
be a program or a collection of data.
The data might be
a year's worth of wind speed measurements, a list of
addresses, or the chapter of a book you are writing.
Because more than one file can often be stored on each
diskette, each file must be identified by a name that
is special to that file, to distinguish it from other
files. The file name
is used for any future reference
to the information in the file.
The file name should be
short (three to eight characters) and it should refer
to the file contents.
For example, a file containing
information on wind velocities might be called WIND.
D.O.S. Commands
The computer expects to receive certain commands from
you. If you send
commands that the computer does not
expect, it will not operate.
Some of the most commonly
used Apple D.O.S. commands and their functions are
listed below. To
send these commands to the computer,
type them on the keyboard and then press the RETURN
key.
Command
Comment
CATALOG This
command causes the computer to print the
names of
all of the files on the diskette.
LOAD This
command puts the information from a
particular
diskette file into the computer's
memory.
LIST LIST
displays the contents of the computer's
memory on
the screen. This allows the user to
read
through the contents of a file that has
been
loaded.
RUN Once a
program has been written, it is of no
use unless
it can be made to operate. RUN
causes the
execution of a program.
DELETE This
serious command permanently removes
information (a file) from the diskette.
Once
the file
is deleted from the diskette, it is
gone.
Be certain that you really do wish to
erase
something before using this command.
NEW This
command causes a program that has been
loaded
into the computer's memory to be
deleted.
SAVE When the
computer is turned off, all information
in its
memory is lost. However, information
stored on
the diskettes is not lost. Use
SAVE to
transfer information from the computer's
memory to
the diskette.
RENAME This
command allows you to change the name of
an
existing file.
LOCK This command
protects an existing file from
being
accidentally or deliberately "written
over"
(revised) or deleted. A locked file can
be
unlocked with the command UNLOCK.
HOME This
command clears all of the writing displayed
on the
screen.
Commands that act on a file (LOAD, RUN, DELETE, and
LOCK) require you to type the file name after the
command and before you press the RETURN key.
For example,
if you ask the computer to carry out the command
DELETE you must also tell it which file to delete.
If
the file name is "BAS13.DAT," then
DELETE BAS13.DAT
will delete the file.
Try typing DELETE without a file
name.
RENAME also acts on a file.
You must include the old
name and the new name being given to the file:
RENAME OLDFILE, NEWFILE
With practice you will know that CATALOG and LIST--and
sometimes RUN--do not require file names to be entered
as part of the command line.
Menus
Computer software instructions are too complex and
cumbersome for most operaters.
For this reason, people
who write computer software often code the instructions
in a table similar to the one given below.
1
SQUARE A SERIES OF NUMBERS
2
READ A FILE ON THE DISKETTE
3
AFRICAN COUNTRIES
4
SILLY KINGDOM
5
QUIT
To use the software, simply select the number corresponding
to the operation that the computer is to be
instructed to do.
All of the complex instructions that
have been written into the software are initiated by
typing this number.
The table is referred to as a
menu. Like the menu
used in a cafe, this menu gives you
a choice of operations.
Password Protection
Sometimes it is desirable to limit the use of certain
programs or systems to specific people.
To ensure that
only authorized people, and no one else, can use the
program, a secret code is given to the authorized user.
This code is called a password.
The computer program
will at some time require you to type the password on
the keyboard. The
program is expecting the password and
if it is entered correctly, the program will continue.
If the expected
password is not entered, the program
will stop.
Use the password to protect your files.
Keep the password
a complete secret.
It is no one else's business
and should not be written or told to anyone.
Even the
computer protects the secrecy of passwords:
they are
not displayed on the screen when they are typed on the
keyboard.
Floppy Diskettes
Diskettes are either 5-1/4 inches or 8 inches in diameter
(Apple uses 5-1/4 inch diskettes), plastic, and
coated with a substance similar to the magnetic coating
on recording tape.
The diskette is contained in a permanently
sealed black cover inside which it turns
freely. This unit is
flexible--it will bend--and so is
referred to as a floppy diskette; other storage disks
exist that are not flexible.
Only floppy diskettes can
be used in the disk drives used in this course.
In
another section of the course you will see and use hard
disks.
Though floppy diskettes are durable and made to be
handled, the following guidelines will help you prevent
damage to them.
1. Though the
diskettes are flexible, they should not
be bent.
2. Do not touch the
exposed portion of the diskette.
Scratches and
fingerprints can delete information
or prevent
accurate recording of new information.
3. Always keep
labels on the outside of the plastic
cover.
The label should clearly describe the
information
stored on the
diskette. When preparing the
label, do not
write on it with a hard point, such
as a ball point
pen or a pencil. Instead, use a
soft, felt-tipped
pen. It is best to write the
information on
the label before sticking the label
on the diskette.
4. High temperatures
(125 [degrees] F or 52 [degrees] C) can cause the
plastic cover to
warp or bend.
5. Keep the
diskettes away from electrical items and
magnets.
The information on the diskette will be
lost if it enters
a magnetic or electrical field.
When a telephone rings, for example, it
produces a
significant
electrical field, so do not store
diskettes near
telephones.
6. When purchased,
each floppy diskette comes in a
small open-ended
envelope for protection. When not
in the disk
drive, the diskette should be replaced
in the envelope.
NOTE: Never remove a
diskette from the disk drive
when the red
"in use" light is on, as this may
cause the
information on the diskette to be
lost.
Diskettes have a natural life-span of approximately 40
running hours.
Considering that a diskette runs for
only a few seconds in each use, 40 hours is a long
time. Even so,
diskettes will eventually wear out, and
they can be damaged.
It is essential to keep at least
one set of duplicates of important diskettes.
There are
special computer programs that will make duplicates of
diskettes. Copies of
important diskettes are often
referred to as "back-up copies" and the
information is
said to be "backed up."
Usually the original diskettes
are put safely away and the back-up copies are used
with the computer.
When the back-up copies wear out, or
are lost or destroyed, the originals are used to make
new back-up copies and then put safely away again.
Editing Files and Programs
No matter how well a program or other file may be
written, it is certain that you will want to make
changes in it at some time.
To do this, you can retype
the entire file or other pieces of information into the
machine with changes made, but this would take much
more time and effort than is necessary.
There is an
easier way. You can
make changes in a file by using an
"editor" program.
Editors can work in several ways, but
the results are the same--a small portion of a file is
changed without rewriting the entire file.
An editor
program is exactly what its name implies.
It will edit
a file or program.
Whenever a computer operator revises
or changes computer files, the operator is using
editing software.
Editing software is an essential part of a computer
system and should be purchased as part of an initial
system. Many
different editing packages are available,
and it is not uncommon to have more than one.
Editors
are often built into the design for a particular software
package. It is
possible, however, to purchase
editors as individual pieces of software.
Variables
Often it is useful to program the computer to carry out
a sequence of tasks without using the specific information
required for the desired results.
If, for example, your computer is programmed with the
specific instruction to add 5 and 7, it would give the
only answer that could logically be expected:
12.
But
what if you wish to add 3 and 8, then add 4 and 1, and
later add 271 and 862?
For each of these cases a new
program would need to be prepared.
There is a better
way. The computer
can be programmed to carry out the
following sequence:
It can then be told to ask you to type the numbers to
be added on the keyboard, then press the RETURN key.
The computer will respond by printing the answer, A,
which will be the numerical sum of the numbers typed on
the keyboard, which are represented by B + C in the
computer program.
In this way, the computer has been programmed one time
with the sequence to be performed (A = B + C).
It
carries out the sequence whenever you wish to do it,
and no reprogramming or editing is needed.
In such a
computer program, the numerical value of A, B, and C is
constantly changing, therefore A, B, and C are known as
variables.
Variables are letters in a computerized sequence that
represent specific values.
However, the specific values
change according to the wishes of the operator.
Data Bases
Computers have made the storage and retrieval of information
fast and easy. As a
result, large amounts of
related information can be put together to meet
specific needs, in collections called data bases.
For
example, the telephone company assembles a large data
base consisting of all the names, addresses, and telephone
numbers of its customers.
The supermarket keeps a
computerized data base of the quantity and price of
each grocery item it has on the shelves.
The Library of
Congress stores bibliographic information on all of its
literature holdings on a computerized data base.
There are many ways to search for information in a
large data base because the computer program is so
versatile that it allows the user to find almost any
information desired.
In VITA's bibliographic data base,
you might, for example, ask the computer to display a
listing of all documents written by a specific author,
or all those on the subject "plastics."
Or you could
find out how many documents VITA has on "wind
power,"
how many new documents were added to the collection
after September 1, 1983, and so on.
One important way to find information in a data base is
by using key words.
Key words are terms that refer to
specific concepts or types of information.
For
example,
if you wish to find information on energy from the sun,
you might direct the computer to look for SOLAR
ENERGY. In another
data base, the key word might be SUN
POWER. The important
thing to remember is that the same
key word always applies to the same type of information.
In VITA's bibliographic data base, each record includes
a list of key words that apply specifically to the
information in that record.
You can instruct the computer
to search through all the records in the data
base, looking through the lists of key words for the
specific words that you have chosen.
When a key word in
a record matches the word you have directed the computer
to look for, the computer displays the entire
record for you. To
use the SOLAR ENERGY example again,
each time a record containing the key word SOLAR ENERGY
is found, that record will be identified for you.
IV. USING THE
MICROCOMPUTER
Thus far we have discussed the basics of microcomputer
operations and functions.
Gaining skill and confidence
comes through actual practice with the computer itself.
This section of the text will guide you through
more important procedures used to maintain and operate
VITA'S bibliographic data base and its skills bank of
VITA Volunteers.
Following the text closely will assist
you in operating the computer so it will perform the
tasks described. An
instructor is also available to
answer questions and assist with problems.
Data Entry
Entering data accurately into the computer is a critical
step in building an efficient, trustworthy computerized
information system.
Data entry is, obviously,
a manual operation and can be, as in all manual systems,
subject to error.
The computer cannot compensate
for operator errors in the data entered.
For example,
if a key word for a document is "wind power," that
word
must be entered accurately and exactly.
If the operator
makes a typing error so that the word is entered as
"wind power," for example, that document will
never be
found when the operator is searching for "wind
power"
documents. Likewise,
use of a similar word such as
"wind generating" instead of the established key
word,
"wind power," will prevent the computer from
finding
the document.
Consistency and accuracy, then, are essential to data
entry. Just as in
manual bibliographic cataloging or
skill coding for the skills bank roster, an authority
file or thesaurus of controlled terms must be kept and
used to ensure consistency in titles, etc.
Similarly,
an authority file must also be kept for such things as
abbreviations, acronyms, publisher addresses, etc.
After each data unit is typed, it must be carefully
checked for accuracy.
Any error must be corrected by
editing the entry.
Only when the unit is correct should
it be entered into the system.
Procedures for Data Entry
The procedures that follow apply to both VITA's
bibliographic
data base and its VITA Volunteer skills
bank. Some of the
procedures will vary (see notes in
the steps outlined) depending upon which data base is
being used and whether the computer in use is a stand
alone system or is connected to the hard disk.
Getting Started. If
you are using the hard disk system,
simply press the switches that turn on the computer and
screen, and proceed to Logging On.
If you are using a
stand alone computer, insert the "program"
diskette
(see the label) in Disk Drive 1 and the "data"
diskette
in Disk Drive 2.
Close the drive gates. Press the
switches that turn on the computer and the screen
monitor. When the
whirring of the disk drive stops and
the red light goes out, you are ready to log on.
Logging On. Follow
the sequence of operations outlined
below. If using the
hard disk system, start with item
a. If using a stand
alone computer, begin with item b.
Screen Displays
User Types
a. PLEASE ENTER YOUR
NAME DOC (bibliographic data
base)
or
SKIL (skills bank)
Press RETURN
b. A>
B:
(don't forget colon)
c. B>
DBMS (Data Base
Management Software)
Press RETURN
d. ENTER LICENSE
NUMBER: 335116
Press RETURN
e. ENTER TODAY'S
DATE
6/19/84 (for example)
(use numbers and
slashes as shown for
month/day/year)
Press RETURN
f. B>>
Entering the Data.
For data entry, you may use either
VITA's bibliographic data base or the VITA skills bank.
The process is similar for both data bases, although
the specific data fields, their names, lengths, and the
information to be entered into each field differ for
each data base.
Study the VOLUNTEER FILE format and the BIBLIOGRAPHIC
DATABASE format in Appendixes B and C, along with the
accompanying descriptions of the field names and space
allocations for each of the two data base formats.
Select the data base you will use, collect the data you
will enter into the computer, and follow the steps
below:
Screen Displays
User Types
a. B>>
ENTER VOL
(skills bank)
or
ENTER FULLREC
(bibliographic data base)
Press RETURN
b. VOLUNTEER FILE
format Type in data
or
VITA
BIBLIOGRAPHIC
DATABASE format
The Cursor, Data Fields, and Key Operations.
Note that
the cursor blinks at the beginning of the first data
field of the form on the screen ([ACCNO] or [NO.]).
Type the number of the document or the Volunteer in the
field and advance to the beginning of the next field by
pressing the RETURN key.
If all spaces in a field are
filled, the cursor will automatically advance to the
next field without the RETURN key.
If the RETURN key is
used in this instance, it will skip a field, requiring
the user to move the cursor back to the beginning of
the field that was skipped.
Move the cursor by using
the left arrow key, which will move the cursor backward.
Some fields in the form are programmed with a "default
value." The
computer has been programmed so that unless
the data entered are different from the answers or
values assigned to those fields, the computer will
automatically enter the answer into the field when the
RETURN key is pressed.
There are a few fields that continue for more than one
line (e.g., SKL1 and SKL2 in the VOLUNTEER FILE or
ABSTRACT in the VITA BIBLIOGRAPHIC DATABASE).
In the
VOLUNTEER FILE, care must be taken to complete the word
at the end of the line.
Hyphens may not be used, nor
can words be split between two lines.
However, in the
BIBLIOGRAPHIC DATABASE, continue entering data when the
right margin of the screen is reached in the ABSTRACT
field. The word
being typed will "wrap" to the next
line. Though a word
may appear broken, since part of it
is on one line and part on the line below, the computer
will put the word back together when the record is
printed. Again, do
not use hyphens.
ABSTRACT consists of two fields.
The cursor will automatically
skip to the second ABSTRACT field when the
first has been filled.
In this case, when the first
field is filled, continue typing even though a word may
be split between the first and second ABSTRACT fields.
If there are too many data for both fields, simply
shorten the data with a slash (/) at the end of the
second field.
When data entry has been completed for a record, press
the RETURN key (or CTRL-E) until the option line
appears at the bottom of the screen:
OPTION: ABORT (A),
CONTINUE (C), DELETE (D), END (E),
PRINT (P), REVISE (R)?
For data entry, only A, C, E, or R are used.
Abort (A) might be used if you discover that you are
duplicating a record you already entered into the computer.
Typing A will display on the screen:
CONFIRMATION
REQUIRED TO ABORT CURRENT RECORD (Y/N)?
Typing Y
(yes) will abort only the record displayed on the
screen and it will not be entered into the computer.
Type C to continue to the next record to be entered.
A
blank form will appear on the screen and a new record
can be typed.
When data entry is completed, type E to end the record
and press the RETURN key.
The record will be entered
into the system, and the computer may be turned off or
used for a different task.
If errors have been made in typing the record, corrections
can be made by choosing the Revise (R) option.
Type R and the cursor will go to the first field.
Press
the RETURN key to move the cursor to the field(s) needing
correction. Then
type CTRL-L until the cursor
reaches the character(s) to be changed.
Should you, by
mistake, go past the point needing correction, move the
cursor back to the proper place by typing CTRL-H.
Type
in the corrections.
If any unwanted characters remain
in the field, remove them by pressing the space bar.
When all corrections have been made, press the RETURN
key until the OPTION line reappears.
Press C to continue
or E to end.
Updating Records.
Records stored in the computer will
sometimes need correcting or updating.
For instance,
VITA Volunteers acquire new skills, change employment,
move to a new address; documents are revised or data
entry mistakes are noticed and need correction.
To update or correct a record already in storage, use
the following procedure:
Log on (see p. 20).
Screen Displays
User Types
B>>
UPDATE VOL WHERE NO.
IS
(type number(s)--if more
than one, separate the
numbers with commas)
Press RETURN
RECORD REQUESTED
OPTION:
REVISE(R),
R,D,N, or E (as
DELETE(D), NO CHANGE(N),
appropriate)
END(E)
Pressing R allows you to make revisions in the record
as described earlier.
To delete the record, type D and
the screen will display:
CONFIRMATION REQUIRED TO
DELETE (Y/N). Type Y
(yes) or N (no) as appropriate. If
you find that the record needs no change, press N and
the next record to be updated will appear on the
screen. When the
last record has been updated, the
screen will show:
ENTER SEARCH CONDITION
WHERE NO. IS (type
OR END (C/R)
number(s))
or
Press RETURN
If all records have been updated, press E.
This will
store the last record entered, and the screen will
again display ENTER SEARCH CONDITION OR END (C/R).
To
end the process, press RETURN and turn off the computer
or proceed to the next task as appropriate.
Printing Data.
Although records can be viewed easily on
the screen, it is often convenient to have a paper, or
"hard" copy of desired records.
The computer can be
attached to a printer that will produce a paper copy of
the information displayed on the screen.
To operate the printer, turn the black knob on the back
of the printer. A
red light will go on. Then turn the
black switch on top of the printer to the right, toward
"On Line."
A second red light will go on.
To activate
the printer, type P (print), which will appear on the
Option line at the bottom of the screen.
In addition to printing records, the printer can also
be programmed to produce charts, graphs, or illustrations
stored in the computer, and these can be printed
in either black or color.
The printer can operate at
fairly high speeds, between 110 and 200 characters per
second, depending upon the setting used for the function
switches.
Data Base Searching
Bibliographic Files.
To assist in searching the "VITA
Bibliographic Data Base," certain computer functions
have been streamlined so that the process is easier to
understand. VITA's
practice makes use of this simpler,
automated procedure.
Special instructions will be provided
for those who wish to carry out searches not
handled by the automated procedures or who wish to
understand more about the logical processes involved.
We recommend these instruments for those of you who
would like to implement a system similar to VITA'S (we
can assist you with hardware/software selections and
development, allowing you to create your own customized
system).
It is worth noting that the smaller size data bases
with which you are working do not require the
complexity of the larger VITA system.
In order to
accommodate certain limits, as well as facilitate
speedy searching, the VITA system operates on
"subsidiary" files.
These are files that have parts of
the total record in them.
For example, in our large
system, the file FULLREC into which you entered
information, is actually broken up into four smaller
data bases to facilitate searching speed and file
limitations. You
will be doing all of your work on a
single file. Your
instructor can provide further
illustrations on this point.
Procedures for Bibliographic Data Base Searching.
Go
through the log-on procedure until you have the
"B>>" prompt on your screen.
Now type HELP DOC1 (C/R).
At the top of your screen the words VITA BIBLIOGRAPHIC
SYSTEM will appear, followed by:
THIS MENU ALLOWS
`STAND-ALONE' OR `ANDING' OF COMMON SEARCH CRITERIA.
The menu of search options shown below will also appear
on your screen.
Note: you may choose to include
key
word searching within each selected option.
Screen Displays
1. Microcategory
("MICNAME") field
2. Author
("AUTHOR") field
3. Microcategory
("MICNAME") and author ("AUTHOR")
fields
4. Title
("TITLE") field
5. Microcategory
("MICNAME") and title ("TITLE")
fields
6. Full data base
key word searching
7. Save search
results for later printing/displaying
8. Print/display
results
9. Quit
Normally, searches are performed by choosing from
options 1 through 6.
At VITA, most searching is first
performed on 1 through 5, and the system has been set
up to respond to these options in the fastest way
possible. You may
choose any option you wish and your
instructors will be happy to show you other searching
techniques not included in the menu.
"ANDING" means
that you are looking for records that satisfy two or
more conditions simultaneously (such as options 3 and
5).
Make your selection now by entering the number (without
the period, ".") and pressing RETURN.
You will then
enter the appropriate information.
If the information
you wish to enter is more than 15 characters long
(including spaces), you may enter only the first 14
numbers or letters followed by an asterisk
("*"). The
computer will then find everything that matches the
first 14 characters.
If the entered information
contains a space, the 14 characters entered must be
enclosed in quotes (").
The characters you do enter
must contain exactly the same punctuation and spacing
as on the record(s) you hope to find.
You will then be asked if you will want to combine the
results of this search with key word searching before
printing or displaying.
There are a couple of reasons
for searching on key words last.
First, the selection
of search option "winnows down" (reduces) the size
of
the data base so that key word searching is done on a
smaller set of data than the entire data base.
This is
important because key word searching is done by
"strings"; that is, the computer looks for the
exact
combination of letters or words you have entered and
this type of search takes longer to complete.
Also, you
may choose to "AND" or "OR" the key
words searched;
that is, you may require either that the records
selected contain all of the key words chosen (AND) or
that they include at least one of them (OR).
To indicate that you wish to continue the search with
the use of the key words, enter "Y" for
"yes." Follow
the directions given you on the screen (type
"SEARCH"
to bring up the string search software).
This section
also asks various questions.
First, it wants the name
of the data base.
Just press RETURN. Next you will
be
asked if you want a hard ("printed") copy of the
results of the search.
Reply "N" (no) by pressing
RETURN. You will be
shown a display of all the field
names (abbreviations mostly).
Then you are asked to
select the fields upon which to perform string searching.
Since we are concerned only with key words, enter
the line number corresponding to this field.
You are then asked to select fields ("elements")
to be
displayed. Select
the default value "ALL" by pressing
RETURN. The next
question is whether you want a result
data base. Since you
will want either to print or
display your results, answer "Y" (yes) by pressing
RETURN.
Finally, you are asked to enter your first search
string. Enter it
exactly the way it appears on your key
word list. You will
then have the opportunity to enter
a second key word.
If you do not wish to enter a second
key word, press RETURN at this point and the search
will begin.
Otherwise, enter the second key word.
You
will then have the choice of either "ANDing" or
"ORing"
the chosen key words (default is "OR") and then
adding
up to a total of 10 key words.
You are asked if you wish to display the selected
records. If you
reply "Y" (yes) you will see all the
information comprising the particular record, although
not in the same form in which you entered it.
If this
is not of interest to you, press RETURN for "N"
(no).
You can later print or display selected records by
choosing 8 on the menu.
After replying "yes" or "no,"
the program begins executing.
If you choose "Y" (yes),
the program will pause after the first record selected
and displayed; it will ask if you wish to stop the
search, find the next word, or continue without
stopping. After
selecting and displaying all the
appropriate records, you will see a count of how many
records were in fact selected.
If you choose "N" (no)
for this question, you will see nothing but a count of
the records selected.
To display, print, or save the data, you must re-enter
the CONDOR software.
Follow the same procedures as
before (type "DBMS," followed by the license
number
"335116," today's date, "B:"--if
necessary--and "HELP
DOC1." You may
perform other menu functions at this
point, or choose option 9 ("Quit") to exit the
program.
VITA Volunteer Files.
To search the VITA skills bank,
called "Volunteer File," certain computer
functions
have been automated to make the process easier to
understand. The
course will make use of this simpler,
automated process.
Special instruction will be provided
for those who wish to carry out searches not handled by
the automated procedures, or who wish to understand
more about the logical processes involved.
This is
recommended for those of you who would like to implement
a system similar to VITA'S (we can assist you with
hardware/software selections and development, allowing
you to create your own customized system).
Go through the log-on procedure (see p. 20) until you
have the "B>>" prompt on your screen.
Now type HELP
VOL1. At the top of
your screen the words "VITA Volunteer
Skillsbank" will appear followed by "This menu
allows "ANding" of search criteria."
You are then given
the choice of selecting various search options:
1. Language
("LA") field
2. Geographical
experience ("GE") field
3. Country
("CNTY") field
4. Country
("CNTY") and geographical experience ("GE")
fields
5. Language
("LA") and geographical experience ("GE")
fields
6. Country
("CNTY") and language ("LA") and geographical
experience
("GE") fields
7. Save search
results for later printing/displaying
8. Print/display
results
9. QUIT
Normally, skills bank searches at VITA are done by
choosing from options 1 throuqh 6.
"ANding" means that
you are looking for volunteers that satisfy both conditions
simultaneously (in the case of 6, all three
conditions simultaneously).
The letters "CNTY, LA, GE"
are the initials used for "country, language, and
geographical experience" fields on the form.
You will
be telling the computer to search for combinations of
these fields when you choose 4, 5, or 6.
Make a selection by entering the number only (without
the period, ".") and pressing RETURN.
You will then be
asked to enter the code for the values in the fields
you have selected to search.
Enter these codes by
consulting your code directory.
You will then be asked if you will combine the results
of this search with searches on the skills fields
(SKL1, SKL2, SKL3, SKL4) before printing or displaying.
(Since the availability of the printer is limited
during the training course, you will usually display
results of your search on the screen, rather than print
them.) There are
several reasons for searching on the
skills fields last.
First, the process of choosing the
search options on the menu "winnows down"
(reduces) the
size of the data base so that skills searching is done
on a smaller set of data rather than the entire data
base. This is
important because the skills searching is
done by "strings"; that is, the computer actually
looks
for the exact combination of letters or words you have
entered and this type of search takes longer to complete.
Also, you will have your choice if you want to
"AND" or "OR" the skills selection; that
is, you may
require either that the volunteer records selected
contain all the skills you have chosen (AND) or that
they indicate at least one of them (OR).
At VITA,
skills searches are usually "ORed" so that the
widest
variety is provided within the previously-selected
language, geographical experiences, country criteria.
To indicate that you wish to continue the search using
the skills fields, simply enter "Y" for
"yes."
When the proqram has finished with the "GE,"
"LA"
and/or "CNTY" searches (options 1-6), it will take
you
into the skills searching part of the program.
Follow
the directions displayed on the screen.
This section also asks you various questions.
First, it
wants the name of the data base.
Since you have not
"saved" (made the computer remember) your search
results under any special name, the computer
automatically places them into a file called
"RESULT."
Since RESULT is the default value given in brackets
when you are asked for the data base name, simply press
RETURN. Next you
will be asked if you want a hard
("printed") copy of the results of the
search. Reply
"N" (no) by pressing RETURN.
You will be shown a
display of all the field names (abbreviations mostly).
Then you are asked to select the fields
("elements")
upon which to perform string searching.
Since we are
concerned only with SKL1, SKL2, SKL3, and SKL4, enter
the numbers corresponding to these fields, separated by
commas (no comma after the last number).
They do not
have to be entered in numerical order.
However, they
will be searched in numerical order.
You are then asked to select fields ("elements")
to be
displayed. Select
the default value "ALL" by pressing
RETURN. The next
question is whether you want a result
data base. Since you
will want to either print or display
your results, answer "Y" (yes) by pressing RETURN.
Finally, you are asked to enter your first search
string. Enter it
exactly the way it appears in your
skills code list.
You will then have the opportunity to
enter a second code.
If you do not wish to enter a
second skill code, press RETURN at this point and the
search will begin.
Otherwise, enter the second code.
You will then have the choice of either "ANding"
or
"ORing the chosen skills (default is "OR")
and then
adding up to a total of ten skills codes.
You are asked if you wish to display the selected
records. If you
reply "Y" (yes) you will see all the
information characterizing the particular record, although
not in the same form in which you entered it.
If
this is not of interest to you, press RETURN for
"N"
(no). You can later
print or display selected records
by choosing 8 on the menu.
After replying "yes" or
"no," the program begins executing.
If you choose "Y"
(yes), the program will pause after the first record
selected and displayed; it will ask if you wish to stop
the search, find the next word, or continue without
stopping. After
selecting and displaying all the appropriate
records, you will see a count of how many
records were in fact selected.
If you choose "N" (no)
for this question, you will see nothing but a count of
the records selected.
To display, print, or save the data, you must re-enter
the CONDOR software.
Follow the same procedures as
before (type "DBMS," followed by the license
number
"335116," today's date, "B:"--if
necessary--and "HELP
VOL1." You may
perform other menu functions at this
point, or choose option 9 ("Quit") to exit the
program.
Sample Volunteer File Search.
An example of a search to
locate specific volunteers follows.
Suppose you want to
find people who have had experience living in Costa
Rica, who speak Spanish, and who have expertise in solar
energy. The
following procedures would be observed:
Screen Displays
User Types
B>>
HELP VOL1
MENU
5
ENTER LANGUAGE ("LA") CODE:
SPA
ENTER GEOGRAPHICAL EXPERIENCE
("GE")
CODE: COS
COMBINE WITH SKILLS FIELDS SEARCHING?
Y
(Computer works, then "B>>" appears
by itself)
SYS
B>
SEARCH
ENTER NAME OF THE DATA BASE
Press RETURN
DO YOU WANT A HARD COPY OF FIELD NAME?
Press RETURN
SELECT ELEMENTS TO SEARCH IN FOR
THE STRING?
22,23,24,25
SELECT ELEMENTS TO DISPLAY WHEN
STRING IS
FOUND Press
RETURN
DO YOU WANT A RESULT DATA BASE?
Press RETURN
ENTER SEARCH STRING 1?
SOLARENER
ENTER SEARCH STRING 2?
Press RETURN
DISPLAY SELECTED RECORDS?
Press RETURN
B>
DBMS
ENTER LICENSE NO.
335116
ENTER TODAY'S DATE
6/19/84
(e.g.)
B>>
HELP VOL 1
ENTER NUMBER
8
DID YOU SAVE YOUR SEARCH RESULT
N
TAKE NOTE OF RECORD NUMBERS
ENTER "P" OR
"D" FOR "PRINTING"
OR
"DISPLAYING"
D
Records are displayed on the screen.
Commercial Data Bases:
DEVELOP (CDC)
There are many hundreds of computerized data bases in
the United States, covering thousands of different subject
areas. Their file
sizes vary greatly, from a few
thousand records to several million.
The number of data
bases available grows at an astonishing rate every year
as publishers prepare new computerized files of information.
The data bases themselves are changing as more
and more producers prepare full text information (e.g.
LEXIS, NEXIS, NEW YORK TIMES) rather than the more
common bibliographic/annotated citations.
Data bases are available to information seekers through
companies referred to as vendors.
The names of some of
the better known vendors whose main frame computers
contain many different data bases are DIALOG, ORBIT,
CDC, BRS, and SDC.
Anyone who has a computer with telecommunications
equipment, and who has access to a telephone,
can search the data bases provided by these (or
other) vendors.
Searching a data base, however, can be quite expensive.
Vendors' charges are based on the particular data
base the user is searching and on the length of time
the user is connected to the vendor's computer.
Charges
can range from $50 per hour to over $100 per hour.
On
top of this, the user must pay a fee for a personal
password that will allow access to the vendor's computer
as well as the cost of telecommunications while
searching a data base.
This can be quite expensive if a
long distance call is required to gain access to the
vendor's computer.
If the user has access to a telecommunications
"net," such as Telenet or Tymnet,
however, the communications costs will be lower.
Utilizing the wealth of information available on these
computerized data bases requires some skill and experience.
Those making best use of this type of resource
need to know something about the content of the various
data bases in order to select those most likely to
yield the required information.
Further, to minimize
the costs involved in searching these commercial data
bases, it is very important to understand the techniques
and commands used by a specific vendor's computer
system and to plan a careful search strategy
before accessing the data base.
Before entering a data base, a user should prepare the
search procedure, i.e. the search strategy.
The search
strategy consists of the search commands and the sequence
in which they will be sent to the computer for
action (the commands used in preparing a search strategy
are discussed below).
The importance of having the
search strategy firmly in mind prior to entering the
data base cannot be overemphasized.
It is not uncommon
for well prepared searches to require half an hour or
more of on-line time connected to the data base computer.
Preparing for such a search can reasonably be expected
to use more than an hour.
The planning time required
will vary with the experience of the data base user,
but irrespective of the amount of planning time required,
if the preparation is done while connected to
the computer, unnecessary on-line charges will occur.
It makes good sense to do as much prior planning as
possible.
In planning a data base search, it is, as mentioned
above, important to know what the vendor's software and
the data base to be searched require of the user.
Because there are many different systems, it is necessary
to study the literature about a data base before
trying to use it.
Most large data base companies have a
search service, where a user describes in words to a
data base expert what it is that he or she is trying to
find. These experts
convert the request into the appropriate
computer commands. A
search service is convenient
for users who are located far from the data base
(such as overseas).
For users in the same country, it
is usually easier and less expensive to gain access to
the data base from a computer terminal equipped with a
modem and communications software in the user's own
office or home.
In this course we will learn basic search techniques
for a data base called DEVELOP, which is owned and
operated by Control Data Corporation (CDC) in Minneapolis,
Minnesota. DEVELOP
is a data base containing
information on appropriate technology that can be
applied to needs in developing regions.
The course
includes a demonstration of the use of DEVELOP with the
Apple equipped with a communications software package
called AE:Pro, which has been developed by Southwestern
Data Systems in San Diego, California.
Key Word Searching.
A list of identifying key words is
appended to each information unit in the DEVELOP data
base. These key
words are confined to those appearing
in the DEVELOP Thesaurus, and are selected in accord
with how well each describes the content of the information
unit. We have
already noted the importance of
key words to a search; an effective searcher must have
a good knowledge of these words.
The searcher should
always check the Thesaurus when preparing a search to
ensure that only key words appropriate to the information
sought are used.
The simplest technique for searching on DEVELOP is to
use the format:
S:KEYWORD where S is the command for
SEARCH and KEYWORD represents any key word the user
chooses. The CDC
computer searches through the key
words of each record.
When it finds the same word that
the user has requested, the computer puts the entire
record of information in a special file called a Result
File. It then
continues searching the data base for
other matching key words.
Each time it finds a match,
the entire record is added to the Result File.
When the
search is completed, all of the information units in
the Result File contain the key word the searcher used
in the key word lists.
The user can then read the
information in the Result File by using the LIST
command, which is described below.
Truncation. If the
DEVELOP searcher uses the command
S:AGRICULTURE, all of the records with the key word
agriculture will be written in the Result File.
However, records using such key words as AGRICULTURAL
DEVELOPMENT, AGRICULTURAL EQUIPMENT, and AGRIBUSINESS
will not be selected.
To broaden a search, one can use the first four letters
of AGRICULTURE, which allows the computer to choose all
keywords that begin AGRI regardless of the letters that
follow. Then all the
records with the key words noted
above will be selected and moved to the Result File.
The command for this technique is S:AGRI/.
The slash character at the end instructs the computer
to accept any characters after the first four, but the
first four must be AGRI.
If the slash is not used, then
the computer will search for the exact keyword, AGRI,
but since there is no such word, no records will be
written to the Result File.
When the slash is used, the keyword is said to be truncated.
Using "AND," "OR," and "AND
NOT." If a DEVELOP searcher
wishes to find information on intercropping marigolds
and tomatoes, the use of only one keyword would not be
very efficient. The
user is not interested in all the
records that pertain to marigolds, nor all those
pertaining to tomatoes.
The user wants only the records
that pertain to both marigolds and tomatoes.
The DEVELOP software does permit the use of several key
words in one search command.
To do so, the key words
must be connected by certain operational words.
The
three permissable operational words and their representative
symbols (indicated in parentheses) are:
AND(*) If two (or
more) search terms are joined
by AND,
only records having both (or all)
terms
in their key word lists will be put
into
the Result File. Records having only
one of
the key words will not be selected.
OR(+) If two
(or more) terms are joined by OR,
records
having any one of the key words
will be
selected.
AND NOT(*-) If two
key words are joined by AND NOT,
information records having the first term
and not
the second will be put into the
Result
File.
The proper way to search for information on intercropping
marigolds and tomatoes in the example mentioned
above is to use the command:
S:MARIGOLD/*TOMATO/, which
uses the operational word AND(*).
If we wanted to find information on pears or apples or
peaches, the command:
S:PEAR/+APPLE/+PEACH/ would
locate all information having one, two, or three of the
key words used and place the units in the Result File.
The command:
S:APPLE/*-FOOD PROCESS/ will select all
the records about apples that do not involve food
processing (processors or other endings).
Translate the following command into your own words:
S:
((APPLE/+PEAR/)*-FOOD PROCESS/)*BOTSWANA
Note that parentheses are used to separate unlike
instructions.
Data base software that handles commands using AND, OR,
and AND NOT is said to use Boolean logic.
This is an
important and powerful feature for data base searching.
It allows the searcher to design sophisticated and
efficient strategies for quickly locating the information
most suited to the user's needs.
The Report Following the Search.
A search does not
begin until the RETURN is pressed following the command.
At that time, the computer begins searching the
records. When it has
finished creating the Result File,
it reports to the user with information in the following
format:
A
E
I L
P Q
R
T W
X =
SET NAME
0
0
0 4
0 0
0
17 1
0 22
S8
The letters across the top of the report refer to the
type of information contained in a record of information.
When the record was entered into the data base by
the data base owner, it was assigned to one of the
categories. The most
frequently assigned types of
information (represented by the letters at the top of
the search report line) are:
Literature (L)
References to published literature or
abstracts of articles, papers, and
reports, with bibliographic citations.
Literature units may also be
bibliographies.
Technology (T)
Descriptions of technology, know-how,
processes, methodologies, or research
in
progress. Technology also includes
discussions of research projects, case
studies, and demonstration projects in
which a problem was addressed and
results were obtained.
Technologies
range from methods for setting up manufacturing
industries to instructions
for
building small solar food dryers.
Who's Who (W)
Descriptions of individuals and organizations
active in the fields covered by
the
data base. These organizations are
usually government related, nonprofit,
or
public service and they do not sell
their expertise or services.
They are
research institutes, information centers,
and
development organizations.
Examples of each of these types of information are
given in Appendixes D, E, and F.
For an explanation of the other assigned types of
information,
see the DEVELOP Search Service User Handbook.
The numbers in the second line tell the data base
searcher how many records of information of each type
are contained in the Result File.
In this case there
are four Literature records, 17 Technical records, and
one Who's Who record.
The next number is the total
number of records in the Result File and the last entry
on the second line is the name of the Result File for
the particular search.
In this case it is S8, which
means that this is the eighth search carried out since
entering the data base.
Reading the Result File.
Each record of information in
the data base contains four parts:
1) the list of key
words, 2) a one- or two-line brief describing, in very
general terms, the contents of the record, 3) the full
abstract of the information, and 4) the name and
address of a contact from whom more details can be
obtained (see Appendix E).
The computer will give the
Result File a particular name for each search; for
DEVELOP the name is the letter S followed by a number.
The first search produces a Result File named S1, the
second search creates S2, and so on.
To read the information
that has been placed in the Result File, the
computer must be sent the command to LIST, which is L,
the contents of S1.
The computer must also know which of the four sections
of each record of information the user would like to
have listed. The
four sections of the information units
(noted above) have identifying symbols:
KEYWORDS S
BRIEF B
ABSTRACT TEXT T
CONTACT
C
These symbols are incorporated into the command to LIST
in the following manner:
LSBTC:S1. This command will
produce a display of the full record for each unit of
information.
However, it is not necessary to list each
of the four parts of all the records.
If the user
wishes to get only a general idea of the content of the
records in the Result File, the briefs alone need be
listed (LB:S1), or perhaps the briefs and the contacts
(LBC:S1) are needed.
Usually there is no reason to list
the keywords.
Using AE:Pro, the information read from the Result File
is stored on a diskette.
From there it can be called
back to the computer memory and then printed on the
printer, which is more efficient and cost effective
than printing the information while on-line, i.e. connected
to the CDC computer.
Computer Software:
Other Applications
As explained earlier, software is the term used to
refer to the programs that make a computer perform the
desired tasks.
Programs are usually stored on disks,
such as a hard disk permanently attached to the
computer, or on floppy diskettes that are inserted into
the computer's disk drive as needed.
All programs or
software packages come with instruction manuals or
other documentation that give the detailed information
necessary to operate and manipulate the programs.
In the United States, the writing and production of
computer software is a burgeoning industry, and there
are programs available for countless numbers of uses.
The sheer volume and array of available software can be
a problem for users anxious to select the best package
for their particular needs.
But talking with people who
have used a software package for the same purpose, as
well as reading computer journals and talking with
knowledgeable software distributors can help in choosing
a satisfactory package.
Several of the many types of software available are
extremely popular because of their utility, flexibility,
and power to simplify tiresome or complex tasks.
For example, there are text writing programs that allow
the user to type long streams of information into the
computer without checking margins, spacing, or headings.
These programs include editors that allow the
user to change, rearrange, update, and correct information,
and automatically produce an accurate, correctly
arranged, and neatly printed document.
Examples of a
page of input into a text writing program and the same
information as the program finally organized it are
given in Appendixes G and H.
The program used is
prepared for the Apple microcomputer and is called
APPLEWRITER.
Financial Records.
Keeping track of expenditures,
credits, debits, and all the other checks and balances
required by a business has traditionally been done
using oversized paper, ledgers, and calculators.
Such
accounting records can be handled by financial bookkeeping
software, sometimes referred to as an electronic
spreadsheet. VITA
uses a very popular one,
VISICALC. VISICALC
not only lets the user keep track of
business financial records, but also permits exploration
of the outcome of various financial alternatives.
Because VISICALC responds quickly to produce and display
requested totals, hypothetical values can be
entered. This
permits the user to see the financial
outcome of options being considered, i.e. it permits
the user to ask questions like "What if. . . ?"
Graphics. Technical
and business operations are often
supported by graphic presentations of information.
Software has been developed that will read data from a
file and produce a graph with related statistical
information. VITA
uses a graphics software package
called APPLE PLOT.
(See Appendix I).
Long Distance Computer Links.
Several of the data bases
that VITA uses are held in computers in other cities.
To use these data bases it is necessary to connect the
distant computer with one of VITA's Apples.
The connection
is easily made using a modem, which connects the
computer to existing telephone lines through which
information can be transferred.
Once the two computers
are connected, communication software separates operating
commands that are meant for the Apple from operating
commands meant for the host computer.
The software
permits commands and information to be sent to the
host. It also
processes information sent from the host
by instructing the Apple how to receive and store it.
The communication software also permits the host computer
to interrupt its operation and then to resume at
the point where it had been interrupted.
Sometimes other computer operators may wish to connect
with VITA'S computers.
A useful feature of the software
VITA uses is that it allows other computers to telephone
the Apple and send operating commands to it.
For
example, someone in California can use a computer and
communication software to call VITA'S system.
The
California user could then search our data bases, send
us a file, or do a number of other things, all from
California. VITA'S
software answers the call when it
"rings" and responds to the commands sent from the
communication
software of the distant computer.
The communication software for these procedures is also
AE:Pro.
Games. A large
number of sophisticated electronic games
has been developed in response to a big demand for
games that challenge the user's mind and reflexes.
VITA
has some simple games that may be demonstrated in this
course. The more
popular ones are SINK THE SHIP (the
player drops bombs from moving airplanes onto moving
ships), NIGHTMARE #6 (the player tries to figure out
the object of the game by making entries on the keyboard),
and HAMARABI (the player rules a kingdom and
must purchase or sell grain and land in order to feed a
growing population).
Try these games and others when
time permits.
Educational Tools.
Many people view the computer as an
excellent device for educating children, and many
educational software packages have been produced.
VITA
has one of the more popular packages, called LOGO.
This
package permits the child to use several geometric
concepts to draw pictures on the monitor screen.
The
emphasis of this package is creativity (drawing pictures
on the screen) and mathematics, but other packages
emphasize spelling, writing, and grammar.
With the appropriate software, computers can be used
for many, many more things than have been presented
here. There is
software to use for drawing up a will,
for betting on an upcoming football match, for monitoring
the operations in your automobile (if you leave the
keys in the ignition and open the door, a computer
activated voice will tell you "The keys are in the
ignition," or if you are about to run out of gasoline,
another voice will inform you).
When attached to a
video scanner, the computer, with the correct software,
can monitor movements in a room.
In this way computers
have been incorporated into security systems for the
protection of property.
The uses to which a computer can be put are limited
only by the imagination of the people who use and
understand them, and to date there is no indication
that human imagination is failing or slowing down.
During the past 10 years, there has been exponential
growth in the number of companies that prepare software.
Many companies are composed of one or two individuals.
It is estimated that in the last five years
there has been an increase of more than 1000 percent in
the sources of software, and though the competition
between these companies has become keen, there are more
new companies established each month than companies
that fail.
V. AUTOMATING AN
Considerations For Computerization:
Myths and Realities
The microcomputer revolution is taking the world by
storm. Whether or
not it holds net benefits for developing
countries is constantly being debated.
There is
no doubt, however, that all countries will be changed
in some way and that all societies are making efforts
to understand and apply the new technologies.
This gives rise to those who are proclaiming that computers
will "save" developing countries and the
organizations
within them. As
costs fall and the technology
increases in power and sophistication, there is hope
that decentralization of access to information and
therefore decision-making will allow developing countries
to become less dependent on the industrialized
nations. At the same
time it is important to understand
that computers are not panaceas for all the problems of
development and will not always nor instantly cause
improved efficiency or profitability in a given
activity or organization.
Computers can be very useful
tools when appropriately applied to certain problems or
activities. But they
should not be viewed as a universal
"technological fix."
During this part of the training course, we will discuss
some of the myths behind computers and their
applications so that those of you who are interested in
or will in fact be installing computers can carry back
realistic ideas about what is and is not possible,
within a particular timetable and cost restraints.
VITA
is going through an intensive process of applying
microcomputers to various organizational functions, and
we feel that our experience may be valuable to share
with others.
Finally, we will suggest questions that
small organizations in developing countries should ask
themselves and their dealers about buying and installing
computer equipment.
We will emphasize likely
situations to be encountered specifically when
installing and operating computers in developing
countries.
The "myths" and "realities" to be
discussed in greater
detail in the course work are outlined briefly below.
1. Myth:
Computers will bring order to management
systems where
chaos has previously existed.
Reality:
Besides applications in communications
such as
teleconferencing, computers are good at two
basic kinds of
activities: computation ("number
crunching")
and performing repetitive, boring
tasks.
They still depend very much on data entry
being done by
human beings. The most successful
computerized
operations replace successful manual
operations that
have grown so large that the costs
in personnel and
processing delays exceed the costs
of
computerization.
2. Myth:
Computerized systems can be "up"
and
"running" in a short period of time.
Reality:
Time varies in getting computer systems
to function properly.
Assuming the hardware has
been correctly
installed, a good commercial word
processing
software package can be operating successfully
by its user
within a few hours. On the
other hand, a
data base management system (for
example, for a
library bibliographic system or
general
ledger/accounting system) can take many
months to
function adequately. This is especially
true if you are
developing system software from the
"ground
up." "Turn-key" systems
(those where the
development work
has already been done) should not
take as much
time. Even so, adaptations still have
to be made and
users have to learn all system
features,
sometimes by trial-and-error, which is a
time-consuming
process. In general, it is advisable
to consider
installation of a "turn-key" system
unless there are
people readily available with the
sophisticated
expertise required for computer
system/software
development.
Hardware
malfunctions and breakdowns are not
unusual,
especially in the equipment "peripheral"
to the
microcomputer (printers, floppy disk drives,
hard disk drives,
interface cards). There is often
no one to blame
for these occurrences; they just
happen.
(In the United States, we talk of
"Murphy's
Law," which
means that something will go wrong when
you least like or
expect it.)
3. Myth:
Computers save money.
Reality:
Some organizations have reported spending
as much as twice
the original budgeted amount for
hardware and
software before the system is truly
functional.
If you are dependent on outside consultants
to make software
changes as system needs
change, costs can
mount further.
While in the long
run computers can save personnel
costs because of
fewer staff requirements, this
doesn't happen
quickly because it takes time to
install a system
and finally attain flawless functioning,
and people are
still needed to run and
maintain the
computer(s). Some small organizations
in the United
States report cost increases, not
reductions, for
as long as two years during and
following
computerization of their office systems.
4. Myth:
An organization wanting to computerize some
or all of its
operations should invest considerable
resources in
choosing the one best hardware-software
combination for
its needs.
Reality:
In the United States there is a maddening
array of hardware
and software from which to
choose.
While this will be less true in other
countries, it is
still probably not worth the time
and effort to
track down every possible combination
before making a
decision. Also, technological
progress in
microelectronics is highly dynamic. It
is simply impossible
to keep track of all the new
products that are
constantly appearing. Better to
do the best
analysis you can and jump in. Besides,
"old"
microcomputers and software don't become
obsolete in the
usual way. If new equipment is
required for more
sophisticated applications, uses
will always be
found for existing equipment.
The nature of
computerized operations is such that
when
microcomputers are acquired for a single
obvious
application, it usually isn't long before
many other
applications are conceived. Indeed,
there have even
been examples in which, in preparation
for
computerization, U.S. companies have
revamped their
work flow and physical environment
such that
computers no longer seemed necessary and
were never
installed, at least not for the original
purpose.
Microcomputers can perform many different
kinds of tasks
and should be thought of as highly
versatile,
"workhorse" tools. But it is
always
necessary to
analyze carefully the problem to be
solved to ensure
that computerization will produce
such economic
benefits as reductions in cost,
increased
production, time savings, a better
quality product
that realizes a higher revenue, or
the like.
5. Myth:
Your computer dealer knows what he is
talking about.
Reality:
Even in the United States, computer
dealers have a
notorious reputation for not being
reliably
knowledgeable about what they're trying to
sell (there are
exceptions, of course). If you
really want to
know how a particular computer or
software
performs, it is best to talk to someone
who is already
experienced with the equipment and
has used it for
the same or similar application. In
most countries
these individuals are readily
identified
through "user groups" that meet
regularly about
just such kinds of issues.
6. Myth:
Everyone will be excited about participating
in the
"computer revolution."
Reality:
This is perhaps obvious, but bears
mentioning.
It would be
reasonable to think that
people are
attracted to a computer if it helps them
do their job more
efficiently and therefore represents
a plus for the
organization overall; or
conversely, that
people are repelled by it if the
difficulties of
getting the computer to work
properly outweigh
the advantages. The decisions on
whether to use or
not to use computers is not
always so
rational, however. Some people may feel
their positions
are threatened because they will be
required to learn
a new technology and/or procedures
they feel ill
equipped to handle. Others may
push to become
literate in computer applications as
a means to
concentrate their own power and authority,
while not making the same knowledge
available
to others.
Managers may be
more concerned with the image-building
effects of using
computers from an organizational
point of view
than with their actual
utility or lack
of utility. Still others may harbor
real fears that
they may somehow damage the equipment
or the data in
some terrible, irretrievable
way (while
possible, this almost never happens when
following
standard operating/installation procedures
outlined in the
accompanying documentation).
There is also the
possibility of deliberately
"sabotaging" the records/data bases of a computer
system for
personal gain and/or to do havoc to the
organization or
persons within it. In short, there
are many reasons
for using or not using computers
within an
organization beyond rational considerations
alone.
These very real human reactions only
underline the
necessity of careful analysis when
considering
computerization. If the benefits are
clear, the human
problems will be solved over time.
7. Myth:
Following operating and installation manuals
carefully is all
that's required to get computer
systems
functioning in developing countries.
Reality:
Remember that most equipment will be
imported from the
industrialized countries, particularly
the United
States. Accompanying manuals
reflect the
operating conditions to be found in
advanced
countries, e.g., clean and stable electrical
power,
air-conditioned office environments
with
low-humidity, dust-free air, etc.
Specific
analyses need to
be made concerning the nature of
electrical power
supplies, the condition and
ambient
temperature of the surrounding air, whether
the computer will
be physically moved frequently,
etc.
Appropriate solutions must be found to
counter
any condition not
in accord with that assumed as
standard by the
original manufacturer (see attached
"Technical
Considerations for Field Use of Microcomputers").
Having access to
a ready supply of
spare parts is a
must. with special care, microcomputer
use in developing
countries can approach the
reliability
already demonstrated in industrialized
nations.
Questions for Potential Users
In order to assist organizations in determining whether
computers can be useful, difficult questions--such as
those given below--should be answered.
Again, the point
is to accomplish a realistic appraisal of the organization's
need and readiness for a small computer.
1. Who on the staff
will have the primary responsibility
of caring for the
computer and making it function
for the needs of
the organization?
2. Will this person
be required to learn all obvious
applications
himself/herself (word processing,
financial
spread-sheets, data base management, programming
in technical
languages--BASIC or FORTRAN,
etc.) before
teaching them to others or will each
user be
encouraged to teach himself/herself?
3. To whom does this
person report? How will he/she
keep superiors
informed? If superiors are not computer
literate, how
does the responsible person
translate and
communicate difficulties in implementation?
4. Will the
organization make the investment for one
or more people on
its staff to learn how to use a
good data base
manager (programmable software at a
level higher than
that of BASIC or FORTRAN) that
can be adapted to
many different applications? Or
does it prefer to
buy specialized software packages
that come closest
to each specific need? Or a combination
of both?
5. Where will the
computer be placed? Is there an
environment in
which the temperature is controlled,
there is little
dust or smoking, and the relative
humidity can be
adjusted? If printers are operated,
will they impair
concentration/performance of
nearby staff?
6. Is power supply
protection adequate? Will data loss
during
unprotected partial or complete power
failure be
catastrophic? What kind of back-up data
system(s) will be
used?
7. Does the
organization have one year to get adjusted
to the machine
and two years before real savings
are expected?
8. If the computer
doesn't work out, is there a way to
bow out
gracefully after six months or a year?
9. What is the
future of the computer-related project?
Where will it/the
organization be in five
years?
10. Who will conduct
an economic cost/benefit analysis
to ensure that
computerization will be the appropriate
solution to the
problems?
11. Who in the
organization's city/country is also
working on the
same ideas? Are they succeeding?
If
not, why not?
12. What is the
worst-case scenario for having a computer?
Can the
organization afford it?
13. Can the
organization get along for another year
without a
computer?
14. Are there other
means to accomplish the same goals?
Questions to Ask Computer Salespeople
Computer sales are highly competitive, and emphasis is
always given to the positive features of a particular
piece of hardware or software.
This often "down-plays"
or omits entirely any drawbacks or trade-offs that
could be critical to a given application.
Questions
such as those below should assist potential buyers in
dealing with computer salespeople.
1.
What is wrong with this machine?
2.
What are the names of three current
customers who
are using the
same machine for the same thing I
will with whom I
can talk?
3.
What kinds of arrangements are there for
maintenance?
What about a
maintenance contract?
4.
Who fixes your machines?
Where are they fixed?
5.
How did you come to sell computers?
Is it just a
"line of
merchandise" (as in many outlets in developing
countries) or is there an institutional
commitment
to supporting
the product once it leaves
the store?
6.
Do you have any experience setting up the
specific
kind of programs
I need?
7.
Who is available to talk to on weekends and evenings
about the
machine? Will you take questions on
technical
problems by phone or in person during
work hours?
If I have to write, how soon, and by
what means can
you get the answer to me? Is there
any charge for
the information?
8.
Are books, literature, classes available
through
your
establishment?
9.
Is there a local users' group for this
machine?
10. What is the
average turnover for this model?
11. How well does it
interface with other equipment?
Can I add a
modem or printer (or other peripheral
equipment) later
if I choose? Which ones?
Do you
sell them?
12. Can I trade
up? Can I trade in?
13. Will you help me
sell my machine if I want to get
rid of it later?
14. Who can help me
adapt software? How much will it
cost?
15. If some software
does not do what you say it does
(or what I
thought you said it does), can I return
or exchange it
for something else?
16. Is
"loaner" hardware/software
available in case of
a catastrophic
failure?
Technical Considerations for Field Use of Microcomputers
Most microcomputer equipment available in developing
countries is produced in industrial nations, reflecting
the operating conditions and natural environments of
those nations. The
following points should be considered
when operating computer equipment in environments
other than those for which it was originally intended.
Please note that these are very technical points concerning
machine operation, power supply, etc.
They
require the attention of a skilled technician.
1.
When you first buy equipment, also buy the
tools,
spare parts,
test equipment, and hardware manuals
(with
schematics).
2.
Reserve a single electric line to your
equipment,
one that is power conditioned.
This is called a
"dedicated
line."
3.
Stock all fuses (of proper amperage) for all
equipment.
4.
Stock spare circuit boards, and/or have
necessary
back-up
equipment.
5.
Stock all needed supplies, including
diskettes,
ribbons, cables,
print heads, paper, transformers,
etc.
6.
Protect equipment from food, drink, tobacco
smoke,
dust, and any
other foreign matter (including
spiders and
mice!).
7.
Keep diskettes in their jackets and keep
back-up
copies.
8.
Inform yourself about computer maintenance
by reading
articles,
equipment manuals, etc., and learn to
diagnose
problems.
9.
If you use an air-conditioned room, seal all
windows
shut, have a
back-up air-conditioner available,
have a spring on
the door to keep it closed,
use a wet bulb
humidity measure and, if necessary,
a dehumidifier
in the room or inside the computer
itself.
10. Keep the
computer away from the air-conditioner
(moisture and
static electricity).
11. Provide a common
"earth" ground between all system
components.
12. Provide adequate
ventilation, e.g. a fan on the
computer or in
the room. However, assure yourself
that dust is not
being sucked into the machine.
13. Consider the use
of power supply regulators in
light of budget
and power needs (condition your
power aid
appropriately).
14. Consider
switchable battery back-up power sources,
so as not to
lose data if power fails.
15. Power on/off
switches can fail. Consider unplugging
instead of using
the switch. This could be important,
especially in
lightning or thunderstorms that
can send large
voltage pulses down the line into
the
machine. However, it is also important
to keep
the computer
connected to a solid earth ground to
prevent static
build-up that can damage the chips.
This is usually
accomplished by keeping the computer
plugged in since
the third wire (now standard
in the United States) is a ground.
In situations
where there is
only a two-wire connection, the
computer could
be safely disconnected if there is
an independent
ground connection made between the
computer and the
earth (only a qualified person
should perform
this).
16. Acquire
information on each piece of hardware's
dependency on
frequency (e.g., between 50 and 60Hz,
or 60hz [plus or
minus] 5 percent).
17. Know the
different tolerance levels (concerning
power
requirements) for each piece of hardware.
APPENDIXES
APPENDIX A
IN OTHER WORDS(*)
acoustic coupler: A
mechanical device that allows a
telephone handset to be connected to a modem (see
modem). The term is
sometimes used to refer to the
entire modem.
address: A way of
identifying any location in the
memory of a computer.
application program:
Software designed for a specific
purpose (such as accounts payable or receivable, payroll,
inventory, etc.).
artificial intelligence:
A specialized field of research
in computer science.
The term refers to the
ability of a computer to perform functions normally
carried out by the human brain (such as reasoning and
learning).
ASCII: The American
Standard Code for Information
Interchange. The
most generally used format for representing
and exchanging textual information among
computers. Under the
code, each of 96 characters
(letters, numbers, and symbols) is given a unique
binary number code (1s and 0s).
assembly language: A
means of communicating with a
computer at a low level.
Assembly language lies between
high-level languages (such as BASIC and Pascal) and
machine language (the 1s and 0s the computer understands
at its most basic level).
Programmers use
assembly language to make efficient use of memory space
and to create a program that runs quickly.
backup: An extra
copy of software, normally kept on
file in case the original program is damaged or lost,.
BASIC: Beginner's
All-purpose Symbolic Instruction
Code. The most used
high-level language for small computers.
baud: A measure of
the speed at which data travels
(normally between a computer and a peripheral or
between two computers).
binary: A numbering
system that uses only 1s and 0s. It
is an efficient way of storing information in a computer
since the hundreds of thousands of microscopic
switches in the computer can only be on (1) or off (0).
bit: A binary digit
(1 or 0).
bootstrap: A piece
of software, usually stored permanently
in memory, that activates other pieces of software
in order to bring the computer from "off" into
readiness for use.
bps: Bits per
second. A measure of data-transmission
speed showing the number of bits of information that
pass a given point in one second.
In small computers,
the most common bps used is 300.
break: An
interruption of a transmission. Most
small
computer keyboards have a Break key that tells the
computer to stop what it's doing and wait for further
instructions.
bubble memory: A new
method of storing information for
a computer using microscopic magnetic bubbles.
Although
the technology was developed almost a decade ago, it is
still expensive and not yet generally available for
small computers.
buffer: An area in
the computer's memory used to temporarily
store information.
When using a printer, a
buffer is needed because the printer operates much more
slowly than the computer.
byte: A sequence of
bits that represents a single
character. In most
small computers, a byte is eight
bits.
CAD/CAM:
Computer-Aided Design/Computer-Aided Manufacturing.
CAD/CAM is normally done on large computers
because large amounts of memory and processing power
are required.
CAI: Computer-Aided
Instruction. Computers used to
teach normally involve a two-way "conversation"
between
the student and the computer; the computer informs the
student of mistakes
as he makes them, and is able to
respond to the
student's demonstrated lack of knowledge.
channel: A path for
the transmission of information
between two points.
character: A single
letter, number, or other symbol. In
a small computer, a character is normally represented
by eight bits (one byte).
chip: A generic term
for an integrated circuit (IC), a
single package holding hundreds or thousands of microscopic
electronic components.
The term comes from the
slices (chips) of silicon of which they are composed.
clock: In a small
computer, a repeating signal (usually
in the range of millions of cycles per second) that
controls the microprocessor "brain."
Each time the
clock sends a pulse, the computer performs a single
task.
command: A word or
character that causes a computer to
do something.
compiler: A piece of
software that takes a series of
commands written in a high-level language and translates
them into a lower-level language more efficient
for the computer to use.
computer network:
Two or more connected computers that
have the ability to exchange information.
computer program: A
series of commands, instructions,
or statements put together in a way that tells a computer
to do a specific thing or series of things.
core memory: An
outdated term for the main memory of a
computer. Although
core memory has been replaced by
semiconductor memory, the term is often used to represent
main memory.
CP/M: Control
Program for Microprocessors. One of the
oldest and most popular operating systems for small
computers. An
operating system is a group of programs
that is often compared to a traffic cop because it
actually controls what the computer is doing by acting
as an intermediary between the hardware and
the software.
Any piece of applications software must be
written for a specific operating system.
CP/M was
introduced in 1975 and has become one of the most
popular operating systems; an estimated 250,000 small
computers use it.
Thousands of specialized application
programs have been written to be used with CP/M.
CPU: Central
processing unit. The heart of a
computer
that controls all operations of all parts of the computer
and does the actual calculations.
CRT: Cathode-ray
tube. A TV-like display used with most
small computers to show the information the computer
has output.
cursor: A position
indicator on a CRT. It's normally a
flashing or nonflashing square or rectangle.
data: A general term
meaning any and all information,
facts, numbers, letters, symbols, etc., which can be
acted on or produced by a computer.
data base: A
collection of related data that can be
retrieved by a computer (such as a mailing list or list
of accounts).
debug: To go through
a program to remove mistakes.
diagnostic: A
specialized program that checks the computer
for problems and tries to isolate any problems
that it finds.
disk: A round piece
of magnetic-coated material used to
store data with greater density, speed, and reliability
than is available on cassettes (see floppy disk).
diskette: See disk.
display: A method of
representing information in visible
form. The most
common displays used with popular
computers are CRTs and printed paper.
documentation: (1)
The instruction manual for a piece
of hardware or software.
(2) The process of gathering
information while writing a computer program so that
others using the program are able to see what was done.
downtime: Any period
of time when the computer is not
available or not working.
dump: To copy all
information available from one form
of storage to another.
edit: To modify or
add data to an existing document or
program.
emulation: A process
by which some computers can run
programs not specifically written for them.
execute: To carry
out an instruction or series of
instructions.
firmware: A term
referring to software that has been
permanently placed in memory--usually into a ROM (read-only
memory).
floppy disk: A disk
storage device made from a thin,
circular piece of magnetic material.
The usual disk
sizes used with small computers are 5-1/4 inch and 8
inch.
flowchart: A common
method of graphically planning what
a piece of software should do before the actual writing
process begins, or for describing what it does after it
is written.
FORTRAN: FORmula
TRANslation. A high-level computer
language used primarily for mathematical computations.
Although FORTRAN is available for some small computers,
it is mainly used with large commercial systems.
garbage: Meaningless
information.
graphics: Pictorial
information in two dimensions.
hard copy: A
printout of information produced by the
computer.
hardware: The
physical part of the computer (such as
the CRT, CPU, memory, etc.), as opposed to software.
hexadecimal: A
number system with the base of 16. It
is
commonly used by programmers to indicate locations and
contents of a computer's memory.
high-level language:
A method of programming that
allows a person to give instructions to a computer in a
form using letters, symbols, or English-like text,
rather than in the 1s and 0s code which the computer
understands.
impact printer: A printer
that produces hard copy by
physically striking a ribbon and paper.
input: The transfer
of data into the computer.
input/output: Called
I/O for short, this is a general
term for the equipment (such as modem or printer) connected
to a computer and the two-way exchange of information
that goes on between the computer and the
peripheral.
instruction: A
command to the computer telling it to do
one specific thing.
integrated circuit:
Also known as a chip, this is a
group of interrelated circuits in a single package.
interactive:
Describes a computer system where a two-way
conversation goes on between the user and the
computer.
interface: A piece
of hardware or software used to
connect two devices (computers and peripherals) that
cannot be directly hooked together.
interpreter: A
computer program which translates a
single line of a high-level language at a time for the
computer.
Interpreters are more convenient but less
efficient than compilers.
iteration: A series
of steps in a program that is
repeated until a condition is satisfied.
(Also called a
loop.)
line printer: A type
of high-speed computer printer
that prints an entire line at a time (instead of a
character at a time).
load: To put data
and/or programs into a computer.
location: A single
specific place within computer
memory where a piece of data is stored.
A location is
usually identified by a number (known as an address).
LSI: Large-scale
integration. A single integrated
circuit which has more than 100,000 circuits in it.
machine language:
The "native language" of a computer;
those fundamental instructions the machine is capable
of recognizing and executing.
The instructions are
represented by binary code (1s and 0s).
memory: Circuitry
and devices that hold the binary 1s
and 0s the computer can access.
Examples are main
memory (integrated circuits), floppy disks, cassette
tape, etc.
microprocessor: The
central processing unit of a computer
(usually in a single integrated circuit) that
holds all the elements for manipulating data and performing
arithmetic calculations.
MIS: Management
information system. The use of a
computer
for providing information useful to managers
(such as inventories, sales, accounts payable and
receivable, etc.).
modem: Short for
MOdulator/DEModulator. An electronic
device that allows computer equipment to send and
receive information through telephone lines.
There are
two major types:
direct-connect modems and acoustic
couplers.
Direct-connect modems usually plug directly
into a telephone wall jack; acoustic couplers use the
telephone handset for sending and receiving information.
network: An
interconnected system of computers and/or
terminals. The
components do not have to be physically
close to one another and are often connected by telephone
lines.
node: A station on a
network. A node can be a computer
or terminal.
operating system:
"Traffic cop" software that oversees
the overall operation of a computer system.
Pascal: A high-level
programming language named after
the seventeenth-century French mathematician Blaise
Pascal.
peripherals:
Equipment (usually hardware) that is external
to the computer itself.
The most common peripherals
used with popular computers are disk drives,
printers, and cassette-tape recorders.
printer: An output
device that produces hard copy.
printout: Hard copy
produced by a printer.
program: (1) A set
of instructions that tell a computer
to do something.
(n.); (2) To prepare the set of
instructions. (v.)
RAM: Random-access
memory. The main type of memory used
in a small computer.
The time required for the computer
to find one piece of information in RAM is essentially
the same no matter where the information is stored.
Also known as read/write memory because data in RAM can
be easily changed.
ROM: Read-only
memory. Memory where information is
permanently stored and cannot be altered.
This form of
memory is also random-access.
RS-232C: A technical
specification published by the
Electronic Industries Association which specifies one
way in which a computer communicates with a peripheral
(such as a modem or terminal).
service contract: A
repair contract. Computer failure
insurance.
software: Programs
or segments of programs. The term
was coined to contrast with hardware--the actual
mechanics and circuitry of a computer.
software house: A
company that writes programs or
customizes programs specifically to the needs of an
individual customer.
system: An organized
collection of hardware and software
that works together.
system software:
General-purpose programs that allow
programmers to write or modify applications programs.
BASIC may be considered part of the system software; so
is the computer's operating system.
telecommunication:
Transmission of data between a computer
and another computer or terminal in a different
location. It can be
done with phone lines, satellites,
radio waves, optical fibers, or other means.
terminal: A piece of
equipment with a keyboard for
input and an output device such as a CRT or printer.
A
terminal is used to communicate with the computer.
timesharing: A
process whereby the facilities of a
single (usually large) computer are shared by a number
of users.
Timesharing requires large amounts of memory
and special software to make it appear that each user
has the whole computer to himself.
track: A section of
a disk or tape.
turnkey system: A
computer system in which all the
hardware and software has been installed.
Theoretically,
all you have to do is turn it on.
volatile memory:
Hardware which requires continuous
electrical power to keep from losing information.
Most
RAM is volatile; ROM is not.
word: A group of
characters or data that occupies one
location in the computer's memory.
word processing: The
entry, manipulation, editing, and
storage of text using a computer.
(*) Reprinted by permission from Popular Computing,
December 1981.
APPENDIX B
VITA BIBLIOGRAPHIC DATABASE
---------------------------
[ACCNO] ___________
[MICNAME]
__________________________________________________________
[MACRO] ______
[MICRO] __________ [PKT]
___ [LA] _______
[AUT] ______
[TITLE]
_______________________________________________________________________
[AUTHOR]
_______________________________________________________
[PUB]
___________________________________________________________________
[PUBADR] ___________________________________________________________________
[SOURCE] _____________________________________________
[PP] ______
[PUBDATE] __________
[PGS] _______ [ILLUS?] ___
[REFS?] ___
[ABSTRACT?] __
[ENTRYDATE] __________
[FICHENO] ______
[ABSTRACT] ____________________________________________________________________
__________________________________________[#]__________________________________
_______________________________________________________________________________
[KEYWORDS] ____________________________________________________________________
___________________________________________
VITA BIBLIOGRAPHIC DATA BASE
Field Names and Space Allocations
ACCNO =
accession number assigned to a document
(seven spaces).
MICNAME =
micro category name under which a document
has
been classified (50 spaces).
MACRO =
Arabic or Roman numeral that identifies
the
macro category under which a document
has
been classified (six spaces).
MICRO =
alpha numeric characters that identify the
micro category under which a document has
been
classified (seven spaces).
PKT(*) =
packet number in which a particular
document
has
been filed (two spaces).
LA(*) =
language in which the document is written
(three spaces).
AUT =
first three letters of the author's last
name--used only in the classification of
books (three spaces).
TITLE =
title of the document (71 spaces).
AUTHOR =
author/s of the document (43 spaces).
PUB =
publisher of the document (64 spaces).
PUBADR =
address of the publisher (64 spaces).
SOURCE =
title of the periodical in which the
article was published, or the series
number of the document (40 spaces).
PP =
page
range of an article or a chapter from
a
periodical or a book (seven spaces).
PUBDATE =
date the document was published (10
spaces).
PGS =
number of pages in the document (four
spaces).
ILLUS? =
if there are illustrations in the document
--Yes or No (one space).
REFS? =
if there are references cited in the
document
--Yes or No (one space).
ABSTRACT? =
if there is an abstract written for the
document--Yes or No (one space).
ENTRYDATE(*) = date
on which data is being entered (eight
spaces).
FICHENO =
microfiche number on which the document
has
been filmed (six spaces).
ABSTRACT =
abstract written for the document.
This
has
two fields (108 spaces, 117 spaces).
KEYWORDS =
keywords assigned to the document (108
spaces).
(*) These fields are programmed with the default values
noted:
Field
Default Value
PKT
P1
LA
ENG (English)
ILLUS?
Y (yes)
REFS?
N (no)
ABSTRACT?
N (no)
ENTRYDATE
Today's date, e.g., 10/5/83
APPENDIX C
+++++++++++++++++++++++++++++ VOLUNTEER FILE
++++++++++++++++++++++++++++++++
[NO.] ______ [ENTRY DATE] ___________ [UPDATE] ________ [CO]
_____
[APL] ____ [FN] ______________ [I] ______ [LN]
____________________ [BYR] ___ [SX] ___
[ADR1] _____________________________________ [ADR2]
__________________________________
[CITY] ____________________ [STE] ______________ [ZIP] _________
[CNTY] _______________
[PHONE] ____________________________________ [OCCP]
_________________________
[MC] ___ [DEG] ______________________________ [FLD]
____________________
*******************************************************************************
[SKL1]
________________________________________________________________________
[SKL2]
________________________________________________________________________
[SKL3]
________________________________________________________________________
[SKL4] ________________________________________________________________________
*******************************************************************************
[LA] ______________________ [GE]
_______________________________________________
[STC-D] ___ [STC-I] ___ [LTC-I] ___ [SI]
_______________________________
[PS]
________________________________________________________________________ [CR]
___
[CMT1]
________________________________________________________________________
[CMT2] ________________________________________________________________________
VITA VOLUNTEER FILE
Field Names and Space Allocations
NO. =
Identification number given to each
volunteer (six spaces).
ENTRYDATE(*) = Date
on which record is first entered on
the
computer (eight spaces).
UPDATE =
Most recent date on which record is
updated (eight spaces).
CO =
Country of birth of Volunteer (three
spaces).
APL =
Volunteer's title - Ms., Mr., or Dr. (four
spaces).
FN =
Volunteer's first or given name (12
spaces).
I =
Initial of volunteer's middle name (three
spaces).
LN =
Volunteer's last or family name (20
spaces).
BYR =
Year of birth--last two numbers only (two
spaces).
SX =
Male or Female--M or F (one space).
ADR1
=
First line of address (32 spaces).
ADR2 =
Second line of address, if applicable (32
spaces).
CITY =
City (18 spaces).
STE =
State (11 spaces).
ZIP =
Zip or alpha-numeric locator code (nine
spaces).
CNTY =
Country (13 spaces).
PHONE =
Business and home phone numbers, so
indicated
by B
or H (31 spaces).
OCCP =
Volunteer's present work (30 spaces).
MC =
Macro category (using VITA Thesaurus
codes) or major area of expertise (three
spaces).
DEG =
Highest academic degrees (limit two) (23
spaces).
FLD =
Specific area(s) of education or training
(23 spaces).
SKL1 =
Volunteer's principal skills (using VITA
Thesaurus codes) (72 spaces).
SKL2 =
Continuation of above (72 spaces).
SKL3 =
Continuation of above (72 spaces).
SKL4 =
Continuation of above (72 spaces).
LA =
Three-letter codes of languages spoken by
Volunteer (20 spaces).
GE =
Three-letter codes of countries and areas
where
Volunteer has worked (limit to five
countries) (49 spaces).
STC-D =
Short-term consulting in home country (one
space).
STC-I(*) =
Short-term consulting outside home country
(one
space).
LTC-I =
Long-term consulting outside home country
(one
space).
SI =
Special interest, entered by code number
(32
spaces).
PS =
Professional affiliations (67 spaces).
CR =
Does the Volunteer have access to a computer
or a computer terminal? (one space).
CMT1 =
Special comments (72 spaces).
(*) These fields are programmed with the default values
noted:
Field
Default Value
ENTRYDATE
Today's date, e.g., 9/10/84
STC-I
Y (yes)
APPENDIX D
DEVELOP LITERATURE UNIT
L565402 UNIT
LISTING. 83/09/18.
83/03/28.
83/03/28.
AGROWASTE
BRIQUETTING
DATE-1981
DEPARTMENT OF ENERGY
FROM-VITA
FUELS FROM BIOMASS
MEDIUM-SCALE TECHNOLOGY
PELLETIZING
VITA-36956
ZL NORTH AMERICA
ZL USA VA
BIOMASS CAN BE COMPACTED AND PELLETIZED FOR USE AS A FUEL
AND AS
ANIMAL FEED.
REED T. AND B. BRYANT. 1978.
DENSIFIED BIOMASS: A NEW
FORM OF SOLID
FUEL. A U.S. DEPARTMENT OF ENERGY
CONTRACT
(NO.
EG-77-C-01-4042). PUBLICATION PREPARED
BY SOLAR ENERGY
RESEARCH
INSTITUTE, GOLDEN, COLORADO (SERI-35).
30 PAGES PLUS
APPENDICES.
BIOMASS IS AN ECONOMICALLY AND ENVIRONMENTALLY ATTRACTIVE
FUEL,
BUT IT IS OFTEN DIFFICULT TO COLLECT, STORE, SHIP, AND
USE. DENSIFYING
BIOMASS TO A SPECIFIC GRAVITY OF 1.0 ELIMINATES MOST OF
THESE
FUNDAMENTAL PROBLEMS AND PRODUCES A UNIFORM, CLEAN, STABLE
FUEL:
"DENSIFIED BIOMASS FUEL" OR DBF.
BEFORE CONVERSION TO DBF, RAW BIOMASS RESIDUES GENERALLY
REQUIRE
PREPARATION: THE
SEPARATION OF NONCOMBUSTIBLES FROM COMBUSTIBLES,
ESPECIALLY FOR SOLID MUNICIPAL WASTE; MILLING; AND
DRYING. ABOUT
5% OF THE ENERGY CONTENT IN RAW BIOMASS CAN BE EXPENDED IN
PREPARATION
AND 1% TO 3% IN DENSIFICATION.
IN ITS DENSIFIED FORM, BIOMASS
CAN BE BURNED IN STANDARD EQUIPMENT WITH REDUCED EMISSIONS
AND
INCREASED HEAT RELEASE AND THERMAL EFFICIENCY.
TESTS HAVE SHOWN
THAT DBF IS AN ACCEPTABLE SUBSTITUTE OR DILUENT IN EXISTING
COAL-FIRED
SYSTEMS. IN
ADDITION, DBF MAY BE USED IN HOME HEATING,
PYROLYSIS, GASIFICATION, AND POWER GENERATION.
BASED ON COMPONENT EQUIPMENT COSTS AND THE INSTALLED COST OF
EXISTING
PLANTS, THE ESTIMATED BREAK-EVEN SELLING PRICE OF WOODEX
PELLETS IS
$1.20 TO $3.40/MBTU OR $19.20 TO $54.40/TON (1981),
DEPENDING ON FEEDSTOCK
COST. WITHIN THAT
COST RANGE, DBF APPEARS TO BE ECONOMICALLY
COMPETITIVE WITH COAL IN SOME MARKETS, PARTICULARLY WHEN
TAKING INTO
ACCOUNT ENVIRONMENTAL ADVANTAGES OF LOW SULFUR CONTENT.
EVEN WHEN
FOREST AND FARM RESIDUES ARE AVAILABLE FOR FUEL PURPOSES, IT
MAY
BE PREFERABLE TO PELLET THE RESIDUES, RATHER THAN COMBUST
THEM
DIRECTLY, BECAUSE OF TRANSPORTATION, STORAGE, AND CAPITAL
INVESTMENT
SAVINGS.
Volunteers In Technical Assistance
1600 Wilson Boulevard, Suite 500
Arlington, VA 22209, USA
PHONE: (703)
276-1800
CABLE: VITAINC
TELEX: 440192 VITAUI
APPENDIX E
DEVELOP TECHNOLOGY UNIT
T565293 UNIT
LISTING. 83/09/18. 83/04/06.
83/06/03.
15.31.31.
DATE-1977
FOOD GRAIN PROCESSING
FOOD PROCESSING EQUIPMENT
FROM-VITA
GRAIN
GRINDING MILL
MEDIUM-SCALE TECHNOLOGY
STONE CUTTING
STONE MILL
UPPER VOLTA
VITA-28743
WEST AFRICA
ZL NORTH AMERICA
ZL USA VA
SPECIFIC INSTRUCTIONS FOR THE CONSTRUCTION OF GROOVES IN
STONE MILL
BURRS ARE GIVEN.
IN THE CONSTRUCTION OF A GRIST MILL IT IS NECESSARY TO PLACE
GROOVES
ON THE COMMON FACES OF THE GRINDING STONES SUCH THAT THEY
DIRECT
MEAL TO THE EDGE OF THE STONES.
A REQUESTOR IN UPPER VOLTA SOUGHT
ASSISTANCE IN UNDERSTANDING THE PRINCIPLES FOR PLACEMENT OF
THE
GROOVES AND IN THE TECHNIQUES FOR MAKING THE GROOVES.
VITA VOLUNTEER EXPERTS PROVIDED THE FOLLOWING ADVICE:
1. DIAGRAMS WERE
PROVIDED WHICH SHOWED SOME OF THE DESIGNS OF
GROOVING, OR
FLUTING, WHICH CAN BE USED.
2. THE UPPER AND
LOWER STONE BURRS SHOULD BE FLUTED EXACTLY THE
SAME.
WHEN THE UPPER BURR IS TURNED OVER AND
PLACED ON TOP OF
THE LOWER BURR,
THE GROOVES WILL BE IN THE CORRECT ANTAGONISTIC
RELATIONSHIP.
3. THE GROOVES
SHOULD BE ANGLED SO THAT ON THE TOP (ROTATING) BURR
THE POSITION OF
THE GROOVE AT THE RIM LAGS BEHIND THE POSITION
OF THE GROOVE AT
THE CENTER.
4. FOR A BURR 48
INCHES IN DIAMETER THE GRINDING GROOVES SHOULD BE
ABOUT 1.5 INCHES
ACROSS AND ALL SHOULD BE THE SAME SIZE.
5. THE SHAPE OF THE
GROOVE IN CROSS-SECTION IS HALF OF A "V" IN
SHAPE.
THE LEADING EDGE (DURING ROTATION) OF THE
GROOVE IS CUT
PERPENDICULAR
INTO THE STONE. THE CUT IS THEN SLOPED
GRADUALLY
TO THE SURFACE AT THE TRAILING EDGE OF THE
GROOVE.
6. FOR A 48 INCH
BURR THE LEADING EDGE OF THE FLUTE NEAR THE CENTER
OF THE STONE
SHOULD BE CUT ABOUT 5/16 INCH DEEP, ABOUT 3/16 INCH
HALFWAY BETWEEN
THE CENTER AND THE RIM, AND 1/32 INCH AT THE
RIM.
THIS CAUSES THE GROOVE TO BE DEEP WHERE THE
GRAIN ENTERS
THE MILL AND TO
BECOME SHALLOWER AS THE GRAIN IS CONVERTED TO
MEAL AND MOVED
TOWARD THE EDGE OF THE STONES. FOR
FINER MEAL,
THE DEPTH OF THE
GROOVE CAN BE MADE SHALLOWER.
7. DRAW THE OUTLINES
OF THE GROOVES ON THE STONES AND WITH A COLD
CHISEL AND HAMMER
CHIP AWAY THE STONE TO FORM THE GROOVES.
THE
RATE OF FLOW OF
MEAL BETWEEN THE BURRS IS REGULATED BY THE RATE
AT WHICH GRAIN IS
INTRODUCED TO THE SYSTEM AND BY THE CONSTRUCTION
OF THE GROOVES.
8. THE BURRS SHOULD
NOT BE ALLOWED TO TOUCH. THAT IS,
ALWAYS
INTRODUCE GRAIN
TO THE SYSTEM IF INSUFFICIENT GRAIN AND MEAL
IS PRESENT
BETWEEN THE STONES, THE OPERATOR CAN HEAR THE GRATING
OF THE BURRS.
IS NOT
AVAILABLE.
(INQUIRY FROM UPPER VOLTA ANSWERED IN 1977)
Volunteers In Technical Assistance
1600 Wilson Boulevard, Suite 500
Arlington, VA 22209, USA
PHONE: (703)
276-1800
CABLE: VITAINC
TELEX. 440192 VITAUI
APPENDIX F
DEVELOP WHO'S WHO UNIT
W565283 UNIT
LISTING. 83/09/18. 82/12/13.
83/02/03.
17.17.15.
CLIMATE
CONSERVATION
DATE-1977
ENVIRONMENT
FORESTRY
FORESTS
FROM-VITA
GHANA
IVORY COAST
NATURAL RESOURCES
RESEARCH AND DEVELOPMENT
RESEARCH INSTITUTE
SOIL
TROPICAL
VEGETATION
VITA-28849
WEST AFRICA
WILDLIFE
ZL NORTH AMERICA
ZL USA VA
THREE INSTITUTIONS WHICH CAN ASSIST VEGETATION STUDIES IN
TROPICAL
WEST AFRICA ARE IDENTIFIED.
THE FOLLOWING INSTITUTION CAN ASSIST WITH VEGETATION WORK IN
WEST AFRICA.
1. CENTRE SUISSE DE
RECHERCHE SCIENTIFIQUE EN COTE D'IVOIRE.
THIS SMALL
LABORATORY FOUNDED IN 1952 ON SWISS INITIATIVE IS
CONCERNED WITH
PROMOTING STUDIES ON THE FAUNA AND FLORA OF THE
REGION.
IT IS SITUATED AT ADIOPODOUME NEAR ABIDJAN.
2. BOTANY
DEPARTMENT, UNIVERSITY OF GHANA, LEGON, GHANA.
SINCE ITS
INCEPTION MANY QUALIFIED BOTANISTS HAVE UNDERTAKEN
RESEARCH IN THIS
DEPARTMENT INTO A WIDE VARIETY OF PROBLEMS.
AS WITH OTHER
INSTITUTIONS IN WEST AFRICA, A GREAT DEAL OF THE
WORK IN THESE
EARLY DAYS HAS BEEN CONCERNED WITH THE COLLECTION,
NAMING AND
PRESERVING OF PLANT SPECIMENS AND THE HERBARIUM
ATTACHED TO THE
DEPARTMENT NOW CONTAINS OVER 50,000 SPECIMENS,
ONE OF THE
LARGEST COLLECTIONS IN WEST AFRICA.
3. DEPARTMENT OF
BOTANY, KWAME NKRUMAH UNIVERSITY OF SCIENCE AND
TECHNOLOGY,
KUMASI, GHANA.
RESEARCH HAS BEEN
INITIATED ESPECIALLY INTO PROBLEMS OF FOREST
ECOLOGY AND
POLLEN ANALYSIS.
(INQUIRY FROM GHANA ANSWERED IN 1977)
Volunteers In Technical Assistance
1600 Wilson Boulevard, Suite 500
Arlington, VA 22209, USA
PHONE: (703)
276-1800
CABLE: VITAINC
TELEX: 440192 VITAUI
APPENDIX G
TEXT WRITING PROGRAM:
INPUT
! lm10
! rm78
! sp1
! cj
OILS AND WAXES
! Ij
Composition and Use
of "Eucalyptus" Oil
"Eucalyptus" oil is composed of six primary
essential
oils. These are listed
below according to
Jacobs (1979) and each
is given with a
brief description of
its use.
! lm18
! sp0
Cineole:
used in pharmaceuticals and stain
removers.
Phellandrene:
used in industry as a solvent
and
floatation compound for separating
metals. Its presence in
essences
intended for pharmaceuticals
is
prescribed by pharmacopoeias.
Terpineol:
used in perfumery.
Eudesmol:
used as a perfume fixative.
Eudesmyl acetate:
used as a substitute
for bergamot
essence. It mixes we
II with
lavender essence.
Piperitone:
used as a raw material for
synthetic
thymol
and menthol production.
! lm10
! sp1
The specific
composition of, "Eucalypt
us" oil varies
among the many species, therefore,
it is impossible to
analyze a
`representative'
species. The results of
two laboratory
studies on "E. globulus"
are given here as
an indication of the
types and
complexity of the compounds which
combine to form
eucalypt oil.
"Eucalyptus
globulus" has been qualitatively
analyzed with a
computerized gas
chromatography-mass spectrometry analyzer
to identify the
oils present (Nashimura
and Calvin,
1979). The oils revealed
were 1,8-cineol;
alpha, beta, and gamma
-terpinene;
beta-pinene; terpinen-4-ol;
linalool oxide;
alpha-gurjuene; aromadendrene;
alloaromadendrene;
globulol (10-hydroxyaromadendrane);
and others.
A quantitative
analysis of this
species, again
using
chromatography, selectively identified
seven compounds in
the following
proportions (Verma
et al., 1978).
APPENDIX H
TEXT
WRITING PROGRAM: FINAL OUTPUT
OILS AND WAXES
Composition and Use of "Eucalyptus" Oil
"Eucalyptus" oil is composed of six primary essential oils.
These are listed below according to Jacobs (1979) and each
is given
with a brief description of its use.
Cineole:
used in pharmaceuticals and stain
removers
Phellandrene: used in industry
as a solvent and
floatation compound for separating
metals. Its presence in essences
intended for pharmaceuticals is
prescribed by pharmacopoeias.
Terpineol: used in perfumery.
Eudesmol: used as a perfume
fixative.
Eudesmyl
acetate: used as a substitute for
bergamot
essence. It mixes well with
lavender essence.
Piperitone: used as a raw
material for synthetic
thymol and menthol production.
The specific
composition of "Eucalyptus" oil varies among the
many species, therefore, it is impossible to analyze a
`representative' species.
The results of two laboratory studies on
"E. globulus" are given here as an indication of
the types and
complexity of the compounds which combine to form eucalypt
oil.
"Eucalyptus
globulus" has been qualitatively analyzed with a
computerized gas chromatography-mass spectrometry analyzer
to
identify the oils present (Nashimura and Calvin, 1979).
The oils
revealed were 1,8-cineol; alpha, beta, and gamma-terpinene;
beta-pinene; terpinen-4-ol; linalool oxide; alpha-gurjuene;
aromadendrene; alloaromadendrene; globulol
(10-hydroxyaromadendrane); and others.
A quantitative analysis of
this species, again using chromatography, selectively
identified
seven compounds in the following proportions (Verma et al.,
1978).
APPENDIX I
APPLE PLOT GRAPH
DAILY OUTPUT
(U.S. GALS) FROM A 14 FT WINDMILL AT 17 M HEAD
<FIGURE>
11p10.gif (600x600)
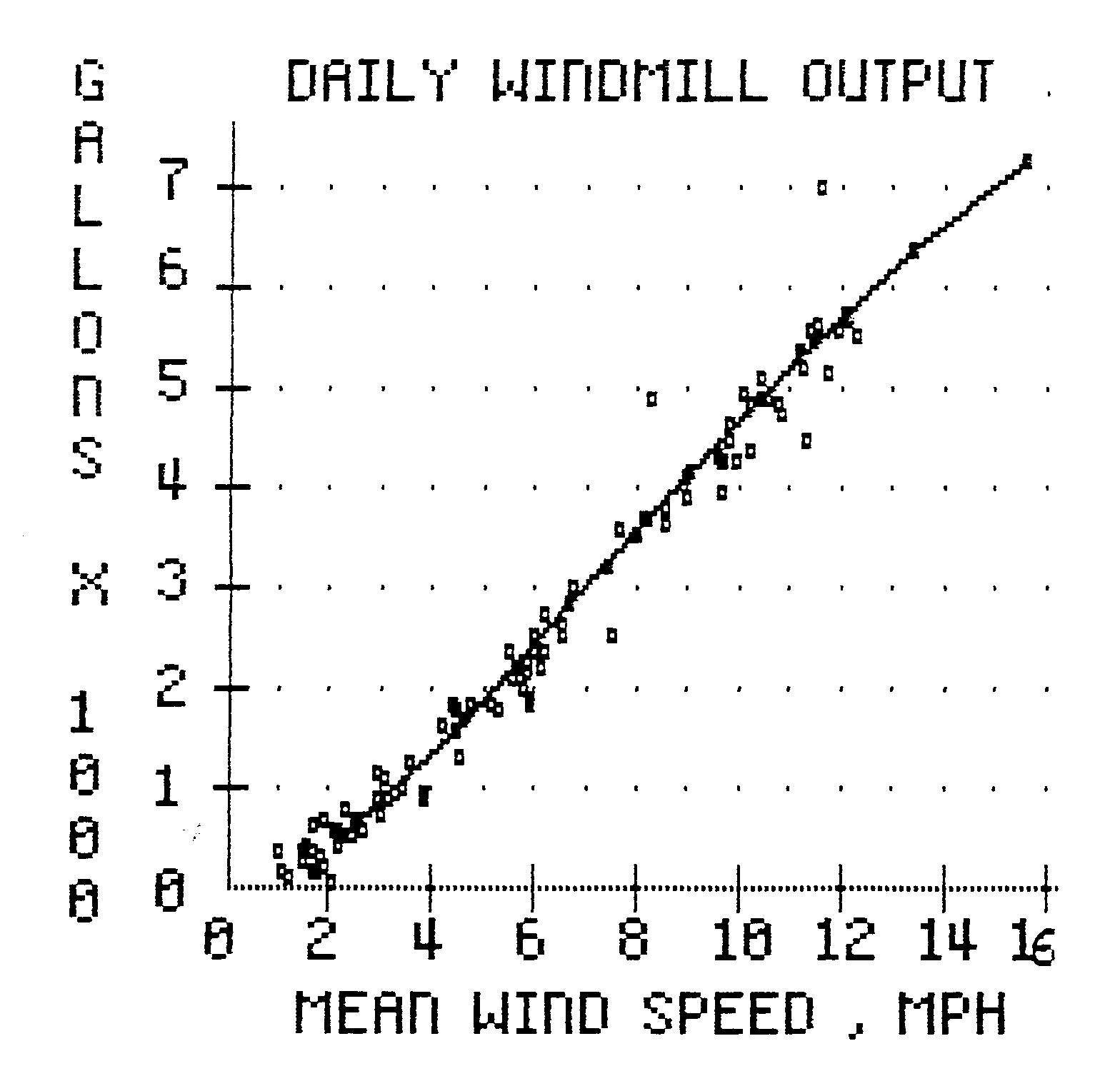
========================================
========================================

